Rohit Mahatara
♦ January 23, 2012
♦ Leave a comment
Recover Your Damaged CDs
I learn an old technique to how to recover damaged or scratched disks
with some lost of data. Here we cover some special technique of how to create a full working CD from the scratched one.
First some tools will be needed:
1. Alcohol 120%
2. UltraISO
3. Windows XP/2000 (not tested on 95/98/me)
3. Small piece of cotton
4. Dry cleaner paper
5. Finally, oil for cooking.
First step – preparing the CD
Get the cotton and drop some water, start cleaning vertically the surface of CD.
Do it 3 times and dry the water with a piece of dry cleaner paper. With a new piece
of cotton, drop some oil for cooking and start to wet the surface like you are
washing the CD with the oil. Dry carefully now. Some particles of oil will stay on the
micro surface of the scratch. It’s okay. Seems the oil helps the laser of the CD/DVD driver
to read the surface again. Sure this will work with small unreadable scratchs – some hard
scratches loose parts of the surface of the CD where we have data and it’s lost forever.
But if it is loosed try anyway. With this tip 80% of the small scratched CD’s could be
recovered.
Second Step – testing the CD
With Alcohol 120% make an ISO – image making wizard – and lets see if the app can
read the loosed surface. In my case Alcohol 120% had recovered 60% of the data.
This is not enough. Have tryed other appz, they do not recover all the data. But the
CD/DVD driver laser CAN recover all data in this case. the data is still there, what we do?
Third step – making the new CD
With the main copy system of windows explorer you can do it. Just create one folder
with the same name of the CD label for future burn reference, and copy the CD content
to the folder. When the CD copy process find the scratch, in majority of the cases, it’s
slow down the reading and will recover ALL loosed data.If not, it just tell you there’s
an unreadable sector. In this case your CD is lost. But it’s not my case, finally
windows explorer got all the data from the scratch and made a copy in the folder.
with the ultraISO, wrote the original CD label, drop the content of the folder and
save as Iso. You can Test the new CD just mounting the iso in the Alcohol 120%. In my
case i did ISO of the two discs from MAX PAYNE 2 and tested installing from the mounted
ISO. Works like a charm. I got the 4 mb lost again. So, I have burned the CD and now i
have a working copy from the scratched one.
Sounds too bizzarre, but works. Course you can jump the cleaning process and try to copy
the content with Windows explorer. But in my case did not work without oil…
Ntfs Cluster Size, better harddrive performance
Cluster is an allocation unit. If you create file lets say 1 byte in size, at least one cluster should be allocated on FAT file system. On NTFS if file is small enough, it can be stored in MFT record itself without using additional clusters. When file grows beyond the cluster boundary, another cluster is allocated. It means that the bigger the cluster size, the more disk space is wasted, however, the performance is better.
So if you have a large hard drive & don’t mind wasting some space, format it with a larger cluster size to gain added performance.
The following table shows the default values that Windows NT/2000/XP uses for NTFS formatting:
Drive size
(logical volume) Cluster size Sectors
———————————————————-
512 MB or less 512 bytes 1
513 MB – 1,024 MB (1 GB) 1,024 bytes (1 KB) 2
1,025 MB – 2,048 MB (2 GB) 2,048 bytes (2 KB) 4
2,049 MB and larger 4,096 bytes (4 KB) 8
However, when you format the partition manually, you can specify cluster size 512 bytes, 1 KB, 2 KB, 4 KB, 8 KB, 16 KB, 32 KB, 64 KB in the format dialog box or as a parameter to the command line FORMAT utility.
The performance comes thew the bursts from the hard drive. by having a larger cluster size, you affectively have a larger chunk of data sent to ram rather than having to read multiple smaller chunks of the same data.
Backing Up the Registry
Backing up your registry from time to time is a pretty good idea. Well, there’s an easy way!
For Win 98 & ME…
1. Click Start /Run and type in “regedit” (no quotes).
2. Next, click the Registry menu, Export Registry File …
3. Select a location from the resulting box and give your backup registry a
name. I use:
like this…Regbackupfile14-11-2006.
That’s it! All backed up.
For XP users…
1. Click Start /Run and type in “regedit” (no quotes).
2. Next, click the File menu, Export
3. Select a location from the resulting box and give your backup registry a
name. Something like:
Regbackupfile14-04-2007.
Just a quick note: by default, Windows backs up the registry when you shut down your machine. The above is probably best used for those (like myself) who like to tinker with registry settings.
Now, how to restore the registry you just backed up…
First, if Windows gets an error when loading your registry, it will automatically revert to its backup, so it should never give you any kind of trouble loading.
OK, but what do you do if you’ve been playing around in your registry and have *really* messed stuff up?
Click the Registry menu (in the Registry Editor) and select Import Registry . Then just point the computer to your back up file.
Oh, one more thing. You can also add the registry to your regular backup routine (you do have a backup routine, don’t you?). Your registry is in two hidden files called “User.dat” and “System.dat”, located in the Windows folder. Just add those two files to your normal backup.
Computer Acronyms
ADSL – Asymmetric Digital Subscriber Line
AGP – Accelerated Graphics Port
ALI – Acer Labs, Incorporated
ALU – Arithmetic Logic Unit
AMD – Advanced Micro Devices
APC – American Power Conversion
ASCII – American Standard Code for Information Interchange
ASIC – Application Specific Integrated Circuit
ASPI – Advanced SCSI Programming Interface
AT – Advanced Technology
ATI – ATI Technologies Inc.
ATX – Advanced Technology Extended
— B —
BFG – BFG Technologies
BIOS – Basic Input Output System
BNC – Barrel Nut Connector
— C —
CAS – Column Address Signal
CD – Compact Disk
CDR – Compact Disk Recorder
CDRW – Compact Disk Re-Writer
CD-ROM – Compact Disk – Read Only Memory
CFM – Cubic Feet per Minute (ft�/min)
CMOS – Complementary Metal Oxide Semiconductor
CPU – Central Processing Unit
CTX – CTX Technology Corporation (Commited to Excellence)
— D —
DDR – Double Data Rate
DDR-SDRAM – Double Data Rate – Synchronous Dynamic Random Access Memory
DFI – DFI Inc. (Design for Innovation)
DIMM – Dual Inline Memory Module
DRAM – Dynamic Random Access Memory
DPI – Dots Per Inch
DSL – See ASDL
DVD – Digital Versatile Disc
DVD-RAM – Digital Versatile Disk – Random Access Memory
— E —
ECC – Error Correction Code
ECS – Elitegroup Computer Systems
EDO – Extended Data Out
EEPROM – Electrically Erasable Programmable Read-Only Memory
EPROM – Erasable Programmable Read-Only Memory
EVGA – EVGA Corporation
— F —
FC-PGA – Flip Chip Pin Grid Array
FDC – Floppy Disk Controller
FDD – Floppy Disk Drive
FPS – Frame Per Second
FPU – Floating Point Unit
FSAA – Full Screen Anti-Aliasing
FS – For Sale
FSB – Front Side Bus
— G —
GB – Gigabytes
GBps – Gigabytes per second or Gigabits per second
GDI – Graphical Device Interface
GHz – GigaHertz
— H —
HDD – Hard Disk Drive
HIS – Hightech Information System Limited
HP – Hewlett-Packard Development Company
HSF – Heatsink-Fan
— I —
IBM – International Business Machines Corporation
IC – Integrated Circuit
IDE – Integrated Drive Electronics
IFS- Item for Sale
IRQ – Interrupt Request
ISA – Industry Standard Architecture
ISO – International Standards Organization
— J —
JBL – JBL (Jame B. Lansing) Speakers
JVC – JVC Company of America
– K —
Kbps – Kilobits Per Second
KBps – KiloBytes per second
— L —
LG – LG Electronics
LAN – Local Are Network
LCD – Liquid Crystal Display
LDT – Lightning Data Transport
LED – Light Emitting Diode
— M —
MAC – Media Access Control
MB � MotherBoard or Megabyte
MBps – Megabytes Per Second
Mbps – Megabits Per Second or Megabits Per Second
MHz – MegaHertz
MIPS – Million Instructions Per Second
MMX – Multi-Media Extensions
MSI – Micro Star International
— N —
NAS – Network Attached Storage
NAT – Network Address Translation
NEC – NEC Corporation
NIC – Network Interface Card
— O —
OC – Overclock (Over Clock)
OCZ – OCZ Technology
OEM – Original Equipment Manufacturer
— P —
PC – Personal Computer
PCB – Printed Circuit Board
PCI – Peripheral Component Interconnect
PDA – Personal Digital Assistant
PCMCIA – Peripheral Component Microchannel Interconnect Architecture
PGA – Professional Graphics Array
PLD – Programmable Logic Device
PM – Private Message / Private Messaging
PnP – Plug ‘n Play
PNY – PNY Technology
POST – Power On Self Test
PPPoA – Point-to-Point Protocol over ATM
PPPoE – Point-to-Point Protocol over Ethernet
PQI – PQI Corporation
PSU – Power Supply Unit
— R —
RAID – Redundant Array of Inexpensive Disks
RAM – Random Access Memory
RAMDAC – Random Access Memory Digital Analog Convertor
RDRAM – Rambus Dynamic Random Access Memory
ROM – Read Only Memory
RPM – Revolutions Per Minute
— S —
SASID – Self-scanned Amorphous Silicon Integrated Display
SCA – SCSI Configured Automatically
SCSI – Small Computer System Interface
SDRAM – Synchronous Dynamic Random Access Memory
SECC – Single Edge Contact Connector
SODIMM – Small Outline Dual Inline Memory Module
SPARC – Scalable Processor ArChitecture
SOHO – Small Office Home Office
SRAM – Static Random Access Memory
SSE – Streaming SIMD Extensions
SVGA – Super Video Graphics Array
S/PDIF – Sony/Philips Digital Interface
— T —
TB – Terabytes
TBps – Terabytes per second
Tbps – Terabits per second
TDK – TDK Electronics
TEC – Thermoelectric Cooler
TPC – TipidPC
TWAIN – Technology Without An Important Name
— U —
UART – Universal Asynchronous Receiver/Transmitter
USB – Universal Serial Bus
UTP – Unshieled Twisted Pair
— V —
VCD – Video CD
VPN – Virtual Private Network
— W —
WAN – Wide Area Network
WTB – Want to Buy
WYSIWYG – What You See Is What You Get
— X —
XGA – Extended Graphics Array
XFX – XFX Graphics, a Division of Pine
XMS – Extended Memory Specification
XT – Extended Technology
Safely Editing The Registry
Windows XP has a vast number of configuration dialogs, but some adjustments can be performed only by directly editing the Registry. Frequently, tips involving Registry tweaks include stern warnings to back up the Registry before making any change. The Windows XP Backup applet can back up the Registry along with other elements of the System State, but the resulting data file can occupy hundreds of megabytes. You’re better off saving a system restore point each time you’re about to edit the Registry. Better still, you can use Regedit to back up only the Registry keys that will be changed.
Click on Start | Run and enter Regedit to launch the Registry editor. To back up an individual key you plan to edit, navigate to the key and right-click on it. Choose Export from the menu, and save the key to a REG file. Open the REG file in Notepad and insert a few comment lines that describe the source and purpose of the tweak. (To create a comment line, simply put a semicolon at the start of the line.)
Now go ahead and make all the changes to Registry keys and values specified by the tip you’re applying. Any time you add a new key or value, make a note of it with another comment line in the REG file. When you’re done, save the REG file and close Notepad.
If later you want to undo this Registry tweak, just double-click on the REG file and confirm that you want to add it to the Registry. This will restore any deleted keys or values and will restore the original data for any values whose data was changed. Note that this will not remove new keys or values that were added; that’s why you need to make comments about such changes.
Right-click on the REG file and choose Edit, which will open it in Notepad. Check for comments about keys or values that were added, and if you find any, use Regedit to delete them. You can delete the REG file itself once you’ve completed this process
FULL FORM OF SOME WORD
AC : alternating current
ALR : Advanced Logic Research
ABM : Atanasoft Berry Computer
ALU : arithmetic logical unite
AT : advanced technology
ATX : advanced technology extended
AFT : Automatic Fine Tuning
AF : Audio Frequency
AM : Amplitude Modulation
AGC : Automatic Gain Control
AFC : Automatic frequency control
AVC : Automatic Volume Control
AVI : Audio Video Grope
ATM : Automated Teller Machine
BHT : Boosted High Tension
DNS : Domain Name Server
DHCP : Dynamic Host Configure Protocol
C/S : Cycle per Second
CRT : Cathode Rey Tube
CTV : Color Television
CVT : Constant Voltage Transformer
CDMA : Code Division Multiple Access
BIT : Binary digit
BCC : Blind Carbon Copy
BIOS : Basic input output system
BPI : Bytes per inch
CD : compact disk
CC : Carbon Copy
CD-ROM : Compact disk read only memory
CD-RW : Compact disk Re-writer
CPU : central processing unite
CU : control unite
COM. : Commercial/Component Object Model
CMOS : Complementary Metal Oxide semiconductor
CAD : computer aided design
COBOL : Common Business Oriented Language
DC : direct current
CGA : coloured graphics adapter
DOS : Disk operating system
DVD : Digital video/versatile disk
DNS : Domain Name Server
DRAM : Dynamic RAM
ENIAC : Electronic Numerical Integrator
and Calculator
EDSAC : Electronic Delay Storage AutomaticComputer
EDVAC : Electronic Discrete Variable Automatic
Computer
E-commerce : Electronic commerce/business
E-mail : Electronic mail
EICAS : Engine Indicator and crew Alert system
EPROM : Erasable programmable ROM
PROM : programmable ROM
EGA : enhanced graphics adapter
FM : Frequency Modulation
FDD : floppy disk drive
FTP : File Transfer Protocol
FMC : Flight management computer
GB : Giga Byte
GHz : Giga hertz
GUI : Graphical User Interface
HDD : Hard disk drive
HTTP : Hypertext Transfer Protocol
HTML : Hypertext Markup Language
HLCIT : High Commission for Information Technology
I/O : Input/output
IBM : International business machine
IC : Integrated circuit
ISO : international standard Organization
ISP : Internet Service Provider
IP : Internet Protocol
IT : Information Technology
CISC : Complex Instruction set computer
JPEG : Joint Photo Export Group
KB : kilo byte
LAN : local area connection
LSI : Large Scale Integration
LCD : liquid crystal display
MAN : Metropolitan area network
MB : mega bytes
MHz : mega hertz
Ms. : Microsoft
Ms-Dos : Microsoft disk operating system
MBA : Master Business Administration
MPEG : Moving Picture Export Group / Motion Picture Export Group
MSI : Medium Scale Integration
MOS : Metal Oxide semiconductor
MODEM : Modulator and Demodulator
MDA : monochrome display adapter
MCGA : multicolour graphics adapter
NCR : National capital Region
NCC : National Computer Center
NME : Nepal Multi Education
NAC : Nepal Airlines corporation
NIC : Network Interface Card
OS : Operating system
OSI : Open System Interconnection
OCR : Optical character recognition
PC : personal computer
PCB : Printed Circuit Board
PDF : Portable Document Format
POP : Post Office Protocol
PS/2 : Personal System/2
POS : Point Sales Terminal
RAM : Random access memory
RISC : Reduced Instruction Set computer
SMPS : Switch Mode Power Supply
SMTP : Simple Mail Transfer Protocol
SRAM : Static Read only memory
SDRAM : Synchronous Dynamic RAM
SVGA : Super video graphics array
TB : Terabyte
TT : Typing Tutor
TCP : Transfer Configure protocol
TUI : Text User Interface
TFT : Thin Film Transistor
UPS : Uninterrupted Power Supply
UNIVAC : Universal Automatic Computer
URL : Uniform Research Locater
ULSI : Ultra Large Integration
ULSIC : Ultra Large Scale Integration Circuit
VDU : Visual Display Unite
VISA : Visitor Intention stay aboard
International Service Associations
VLSI : Very Large Integration
WHO : World Health Origination
WWW : World Wide Web
WAN : Wide Aria Network
XT : Extra/Extended Technology
Introduction of Special Key
~ = Tiled key
! = Exclamation
@ = At the rate
# = Hash
$ = Dollar
% = Percentage
^ = Carat
& = And
* = Asterisk or star mark
( ) = Parentheses
– = Dash
_ = Underscore
| = Vertical mark or pipeline
; = Semicolon
: = Colon
‘…’ = Single quite mark (smart)
“…” = Double quite mark (smart)
‘ = Single quite (straight),Apostrophe
” = Double quite mark (straight)
Inverted Kamas
/ = Forward Slash
\ = Back slash
= Back Space
< = Less than
> = Greater than
= Arrow key
= Enter key
. = Dot (Full Stop)
Application file name of some programs:
typshala.exe : Typical typing programs
tt?.Exe/tt.exe : typing tutor
wordpad.exe : simple word processing Program (word pad)
notepad.exe : simple word processing program (note pad)
calc.exe : calculator
mspaing.exe : Microsoft paint
command.com : dos prompt
winword.exe : Microsoft word
excel.exe : Microsoft excel
powerpnt.exe : Microsoft power point
Msaccess.exe : Microsoft access
pm65.exe/pm70.exe : adobe PageMaker 6.5/7.0
coreldrw.exe : Corel draw
photoshp.exe
photoshop.exe : adobe Photoshop 6.0/7.0
msoffice.exe : shortcut bar
frontpg.exe : Microsoft front page
charmap.exe : character map
mplayer.exe
wmplayer.exe
wmplayer2.exe : media player
cdplayer.exe : cd player
explore.exe : windows Explorer
flash.exe : freehand flash
iexplore.exe : Internet Explorer
msimn.exe : Outlook express
SYSTEM SURTCUT KEY
Close : Alt+f4, Alt +spacebar +C
Close Windows : Control+Q
Restore down : Alt +spacebar +R
Maximize : Alt +spacebar +X
Minimize : Alt +spacebar +N
Shutdown : windows logo +UU
Restart : windows logo +U+R
Stand by : windows logo +U+S
Lock : windows logo +L
Log off : windows logo +LL
Run : windows logo +R
Computer open : windows logo +E
Search : windows logo +F
NEPAL MULTI EDUCATION INSTITUTE & I.T SOLUTION E-mail: rohitmc6@gmail.com 9847897410 460029
Prepared by Rohit mahatara chhetri Dharmawoti-1 Bagdula pyuthan
Web Site : https://nmeiit.wordpress.com/
Rohit Mahatara
♦ January 22, 2012
♦ Leave a comment
Installation Under Windows XP
Please follow the following instructions to install the keyboard layout under windows XP or above.
STEP 1:
Enabling Complex Script in the system in Windows XP
– Go to Control Panel.
– Click on the “Date, Time, Language, and Regional Options”.
– Click on the “Regional and Language Options”.
– On the Languages tab, check the “Complex script and right-to-left languages” checkbox to install the complex script in the system. When you click Ok ,you’ll be asked the Windows XP CD. (You will need Windows XP CD to complete the installation).
– After installing the complex script you’ll be asked to restart the computer.
– Click yes to restart your computer.
STEP 2:
After enabling the Complex Script, you can install 2 keyboard Layout Drivers :
1 . Nepali Unicode traditional
-With this keyboard layout you can type normally as in old fonts but with some keys altered and rearranged with new typing style.
-To view the keyboard layout of Nepali Unicode traditional layout, click here.
– To download the Nepali Unicode traditional, click here.
2 . Nepali Unicode Romanized
– Nepali Unicode Romanized is the new Layout with the keys rearranged as the Romanized keyboard like ? in k and ? in s, so as to facilitate the English users to type Nepali.
– To view the keyboard layout of Nepali Unicode Unicode Romanized, click here.
– To download the Nepali Unicode Romanized, click here.
After you click any one of the keyboard layout driver above, it will ask you to save or open the program. when you click save, it will save the downloaded file to the specified folder. Please extract the zipped downloaded files to the new folder. Open the folder where you have extracted the zipped files. Run setup program from the folder to install the desired keyboard layout driver.
Then the main setup program will start .
Follow the instruction of the setup program .
Click on the close to close the installation.
STEP 3:
To configure the keyboard settings For Nepali Unicode (Traditional), Please follow the following instructions :
– Go to the “Date, Time, Languages, and Regional Options” on the control panel again.
– Click on the “Regional and Languages Options”
– Click on the Languages Tab
– Click on the Details button
– In the installed services, click on the Add button
– In the Input Language, select Sanskrit
– In the Keyboard layout/IME, select Nepali Unicode
– Click Apply to save the changes.
To configure the keyboard settings For Nepali Unicode (Romanized) ,Please follow the following instructions :
– Go to the “Date, Time, Languages, and Regional Options” on the control panel again.
– Click on the “Regional and Languages Options”.
– Click on the Languages Tab.
– Click on the Details button.
– In the installed services, click on the Add button.
– In the Input Language, select Sanskrit.
– In the Keyboard layout/IME, select Nepali Unicode (Romanized).
– Click Apply to save the changes.
To learn new typing style with these keyboard layouts, please CLICK HERE .
————————————————————————————————
Change The Storage Location Of ‘my Documents’, a bit safer for when your PC crashes….
————————————————————————————————
Normally windows saves the “my Documents” folder on your system-drive [the drive you have installed your operating system]. But when you right-click on it and go to properties, you can change the location where you want windows to save your Documents folder.
You should have a partition set up with just windows on it, and all your things you want to keep are on different partitions/disks. So now you can put My Documents on another partition than where you have windows installed. If windows screws up and you have to format your system-drive again, your documents will be spared at least…
————————————————————————————————
Speeding up menus in XP
————————————————————————————————
Go to Start –> Run –> Regedt32
Go to HKEY_CURRENT_USER\Control Panel\Desktop
Locate the key called “MenuShowDelay” and it is probably set to 400.
Change that value to 150.
Reboot your computer.
10 reasons why PCs crash U must Know
You have just been struck by the Blue Screen of Death (BOD). Anyone who uses Mcft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
1. Hardware conflict:
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start -> Settings -> Control Panel -> System-> Hardware -> Device Manager.
Often if a device has a problem a yellow ‘!‘ appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as ‘IRQ holder for PCI steering’. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a sound card, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Mcft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
2. Bad RAM:
RAM (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programmes.
3. BIOS settings:
Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up[this is how we can get into BIOS].
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer’s display.
Mcft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to ‘yes’ to allow Windows to do this.).
4. Hard disk drives:
After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start -> Programs -> Accessories -> System Tools ->Disk Defragmenter
This will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
Fire up the Task Scheduler from Start -> Settings -> Control Panel -> Scheduled Tasks.
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimization. This can be adjusted by going to
- Right Click on My Computer icon in your Start Menu, and choose Properties.
- Click on the Hardware Tab in the System Properties screen, and click the Device Manager button.
- Double Click the “IDE ATA/ATAPI controllers” category to see the channels underneath it.
- Double-click each IDE channel that is present and make sure that “DMA if available” is selected under the advanced settings tab.
- Reboot your computer.
Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDisk
Otherwise assign the Task Scheduler to perform this operation.
5. Fatal OE exceptions and VXD errors:
Fatal OE exception errors and VXD errors are often caused by video card problems.
These can often be resolved easily by reducing the resolution of the video display. Go to
* Start -> Settings -> Control Panel -> Display -> Settings
Here you should slide the screen area bar to the left. Take a look at the colour settings on the left of that window.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device Manager
Here, select the ‘+’ beside Display Adapter. A line of text describing your video card should appear. Select it and Right click -> properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
As ever, the most common cause of problems relating to graphics cards is old or faulty device drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card’s manufacturer on the internet and search for the most recent drivers for it.
6. Viruses:
Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove Programs
Here, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer.
An excellent antivirus programme is McAfee VirusScan by Network Associates. Another is Norton AntiVirus.
7. Printers:
The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer’s performance.
If the printer is trying to print unusual characters, these might not be recognized, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer’s default settings and you may be able to carry on.
8. Software:
A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the programme in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use System Mechanic by iolo technologies to clean up the System Registry and remove obsolete entries. It works on Windows 95, Windows 98, Windows 98 SE (Second Edition), Windows Millennium Edition (ME), NT4 and Windows 2000.
Read the instructions and use it carefully so you don’t do permanent damage to the Registry. If the Registry is damaged you will have to reinstall your operating system. System Mechanic can be obtained from www.iolo.com.
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message “Starting Windows” press F8. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn’t work.
Remember to restore all the BIOS settings back to their former settings following installation.
9. Overheating:
Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
One remedy is to get a bigger better fan and install it on top of the CPU. Specialist cooling fans/heatsinks are available in the market.
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
10. Power supply problems:
With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.
How to Bypass BIOS Passwords
BIOS passwords can add an extra layer of security for desktop and laptop computers. They are used to either prevent a user from changing the BIOS settings or to prevent the PC from booting without a password. Unfortunately, BIOS passwords can also be a liability if a user forgets their password, or changes the password to intentionally lock out the corporate IT department. Sending the unit back to the manufacturer to have the BIOS reset can be expensive and is usually not covered in the warranty. Never fear, all is not lost. There are a few known backdoors and other tricks of the trade that can be used to bypass or reset the BIOS
DISCLAIMER
This article is intended for IT Professionals and systems administrators with experience servicing computer hardware. It is not intended for home users, hackers, or computer thieves attempting to crack the password on a stolen PC. Please do not attempt any of these procedures if you are unfamiliar with computer hardware, and please use this information responsibly. LabMice.net is not responsible for the use or misuse of this material, including loss of data, damage to hardware, or personal injury.
Before attempting to bypass the BIOS password on a computer, please take a minute to contact the hardware manufacturer support staff directly and ask for their recommended methods of bypassing the BIOS security. In the event the manufacturer cannot (or will not) help you, there are a number of methods that can be used to bypass or reset the BIOS password yourself. They include:
Using a manufacturers backdoor password to access the BIOS
Use password cracking software
Reset the CMOS using the jumpers or solder beads.
Removing the CMOS battery for at least 10 minutes
Overloading the keyboard buffer
Using a professional service
Please remember that most BIOS passwords do not protect the hard drive, so if you need to recover the data, simply remove the hard drive and install it in an identical system, or configure it as a slave drive in an existing system. The exception to this are laptops, especially IBM Thinkpads, which silently lock the hard drive if the supervisor password is enabled. If the supervisor password is reset without resetting the and hard drive as well, you will be unable to access the data on the drive.
——————————————————————————–
Backdoor passwords
Many BIOS manufacturers have provided backdoor passwords that can be used to access the BIOS setup in the event you have lost your password. These passwords are case sensitive, so you may wish to try a variety of combinations. Keep in mind that the key associated to “_” in the US keyboard corresponds to “?” in some European keyboards. Laptops typically have better BIOS security than desktop systems, and we are not aware of any backdoor passwords that will work with name brand laptops.
WARNING: Some BIOS configurations will lock you out of the system completely if you type in an incorrect password more than 3 times. Read your manufacturers documentation for the BIOS setting before you begin typing in passwords
Award BIOS backdoor passwords:
ALFAROME ALLy aLLy aLLY ALLY aPAf _award AWARD_SW AWARD?SW AWARD SW AWARD PW AWKWARD awkward BIOSTAR CONCAT CONDO Condo d8on djonet HLT J64 J256 J262 j332 j322 KDD Lkwpeter LKWPETER PINT pint SER SKY_FOX SYXZ syxz shift + syxz TTPTHA ZAAADA ZBAAACA ZJAAADC 01322222
589589 589721 595595 598598
AMI BIOS backdoor passwords:
AMI AAAMMMIII BIOS PASSWORD HEWITT RAND AMI?SW AMI_SW LKWPETER A.M.I. CONDO
PHOENIX BIOS backdoor passwords:
phoenix, PHOENIX, CMOS, BIOS
MISC. COMMON PASSWORDS
ALFAROME BIOSTAR biostar biosstar CMOS cmos LKWPETER lkwpeter setup SETUP Syxz Wodj
OTHER BIOS PASSWORDS BY MANUFACTURER
Manufacturer Password
VOBIS & IBM merlin
Dell Dell
Biostar Biostar
Compaq Compaq
Enox xo11nE
Epox central
Freetech Posterie
IWill iwill
Jetway spooml
Packard Bell bell9
QDI QDI
Siemens SKY_FOX
TMC BIGO
Toshiba Toshiba
TOSHIBA BIOS
Most Toshiba laptops and some desktop systems will bypass the BIOS password if the left shift key is held down during boot
IBM APTIVA BIOS
Press both mouse buttons repeatedly during the boot
——————————————————————————–
Password cracking software
The following software can be used to either crack or reset the BIOS on many chipsets. If your PC is locked with a BIOS administrator password that will not allow access to the floppy drive, these utilities may not work. Also, since these utilities do not come from the manufacturer, use them cautiously and at your own risk.
Cmos password recovery tools 3.1
!BIOS (get the how-to article)
RemPass
KILLCMOS
——————————————————————————–
Using the Motherboard “Clear CMOS” Jumper or Dipswitch settings
Many motherboards feature a set of jumpers or dipswitches that will clear the CMOS and wipe all of the custom settings including BIOS passwords. The locations of these jumpers / dipswitches will vary depending on the motherboard manufacturer and ideally you should always refer to the motherboard or computer manufacturers documentation. If the documentation is unavailable, the jumpers/dipswitches can sometimes be found along the edge of the motherboard, next to the CMOS battery, or near the processor. Some manufacturers may label the jumper / dipswitch CLEAR – CLEAR CMOS – CLR – CLRPWD – PASSWD – PASSWORD – PWD. On laptop computers, the dipswitches are usually found under the keyboard or within a compartment at the bottom of the laptop.
Please remember to unplug your PC and use a grounding strip before reaching into your PC and touching the motherboard. Once you locate and rest the jumper switches, turn the computer on and check if the password has been cleared. If it has, turn the computer off and return the jumpers or dipswitches to its original position.
——————————————————————————–
Removing the CMOS Battery
The CMOS settings on most systems are buffered by a small battery that is attached to the motherboard. (It looks like a small watch battery). If you unplug the PC and remove the battery for 10-15 minutes, the CMOS may reset itself and the password should be blank. (Along with any other machine specific settings, so be sure you are familiar with manually reconfiguring the BIOS settings before you do this.) Some manufacturers backup the power to the CMOS chipset by using a capacitor, so if your first attempt fails, leave the battery out (with the system unplugged) for at least 24 hours. Some batteries are actually soldered onto the motherboard making this task more difficult. Unsoldering the battery incorrectly may damage your motherboard and other components, so please don’t attempt this if you are inexperienced. Another option may be to remove the CMOS chip from the motherboard for a period of time.
Note: Removing the battery to reset the CMOS will not work for all PC’s, and almost all of the newer laptops store their BIOS passwords in a manner which does not require continuous power, so removing the CMOS battery may not work at all. IBM Thinkpad laptops lock the hard drive as well as the BIOS when the supervisor password is set. If you reset the BIOS password, but cannot reset the hard drive password, you may not be able to access the drive and it will remain locked, even if you place it in a new laptop. IBM Thinkpads have special jumper switches on the motherboard, and these should be used to reset the system.
——————————————————————————–
Overloading the KeyBoard Buffer
On some older computer systems, you can force the CMOS to enter its setup screen on boot by overloading the keyboard buffer. This can be done by booting with the keyboard or mouse unattached to the systems, or on some systems by hitting the ESC key over 100 times in rapid succession.
——————————————————————————–
Jumping the Solder Beads on the CMOS
It is also possible to reset the CMOS by connecting or “jumping” specific solder beads on the chipset. There are too many chipsets to do a breakdown of which points to jump on individual chipsets, and the location of these solder beads can vary by manufacturer, so please check your computer and motherboard documentation for details. This technique is not recommended for the inexperienced and should be only be used as a “last ditch” effort.
——————————————————————————–
Using a professional service
If the manufacturer of the laptop or desktop PC can’t or won’t reset the BIOS password, you still have the option of using a professional service. Password Crackers, Inc., offers a variety of services for desktop and laptop computers for between $100 and $400. For most of these services, you’ll need to provide some type of legitimate proof of ownership. This may be difficult if you’ve acquired the computer second hand or from an online auction.
Breaking into Win XP without passwords
Because of the security features built into Windows XP, it is virtually [not actually ] impossible to get back into the system without the password.
You have several options to try and get around this problem.
If you have access to another user account with administrator rights, you can use that account to change the password
of the account that is locked out. You can also use the default Administrator account that is built into Windows XP.
First you need to boot the system into Safe Mode.
1.Restart your system.
2.When you see the blue Dell globe or screen, press the ( F8 ) key about 3 times a second.
3.You should get the Windows startup menu. Use the (Up or Down) arrow keys to highlight (SafeMode)
4.Press (Enter) on (Safe Mode), then press (Enter) on (Windows XP).
5.The system should boot to Safe Mode.
Once you are at the Account Log on Screen, click on the icon
for the user account with administrator rights, or click on the icon
for the administrators account.
Note: For Home the Administrator account isn’t normally shown & in Safe Mode you have to press Ctrl+Alt+Delete keys twice to show.
For PRO you can do this in normal mode
When the system has booted to the desktop, use the following steps to change the accounts password.
1.Click Start, Control Panel, Administrative Tools.
2.Click Computer Management.
3.Double click Local Users and Groups, double click the folder Users.
4.Right click on the account name that is locked out, and click on Set Password.
5.You may get a warning message about changing the password, simply click proceed.
6.Leave the New Password box blank, also leave the Confirm Password box blank.
7.Click OK, and OK again.
8.Then close all Windows, reboot the system and try to log in.
Now there are also applications that can recover the password for you.
The following companies provide these applications at a cost.
iOpus® Password Recovery XP here.
LostPassword.com, here.
Asterisk Password Recovery XP v1.89 here.
Windows XP / 2000 / NT Key here.
Now consider a situation, where you have all the user accounts including default ‘administrator’ account has been kept password protected. Seems like trouble????
Partitioning Your Harddisk With Fdisk
Partitioning your Hard Disk:
Partitioning involves creating logical units on your hard drive that are then addressed as different drive letters. Not only does it help to organize your data (program files on one drive, games on another, documents on another) but also to speed up your PC. This is so because the drive head has to move a lesser distance for accessing data within one partition. You can also have different filesystems and OS’s on the same hard drive.
Partitioning can be done using ‘fdisk’ in DOS/Windows 9x or ‘disk management’ in Windows 2000/ NT/XP. We will describe the procedure for fdisk, since disk management is GUI driven and the basics otherwise remain the same. While several other commercial packages like Partition Magic are available, these utilities (fdisk, computer management) are bundled with their respective OSs. You need a bootable floppy with fdisk.exe, format.com, and sys. com utilities. Before starting, decide how many partitions you want to create and their sizes. You can create one primary and one extended partition using the DOS fdisk. The extended partition can then have multiple logical partitions. Boot your machine using the bootable disk, and do the following.
Run fdisk. The utility will show you a numbered menu from where you can create, view, or delete partitions. The utility first asks you whether you want to enable large disk support. Type Y (for yes) and press enter if your hard-drive capacity is more than 4 GB. Large disk support creates a FAT32 partition, which can be greater than 2 GB
Select the first option from fdisk menu to create a primary partition. Specify the partition size in megabytes or percentage size when prompted for it.
Similarly, create an extended partition. Extended partitions by themselves do not appear as drive letters. Instead, logical partitions must be created in them, which are then assigned drive letters.
Exit fdisk and reboot the computer. Fdisk automatically assigns drive letters to all the partitions. You’ll need to format each partition in order to use it. Use format.com for the same
Your hard drive is now ready for taking an OS.
Firefox Speed Tweaks
Yes, firefox is already pretty damn fast but did you know that you can tweak it and improve the speed even more?
That’s the beauty of this program being open source.
Here’s what you do:
In the URL bar, type “about:config” and press enter. This will bring up the configuration “menu” where you can change the parameters of Firefox.
Note that these are what I’ve found to REALLY speed up my Firefox significantly – and these settings seem to be common among everybody else as well. But these settings are optimized for broadband connections – I mean with as much concurrent requests we’re going to open up with pipelining… lol… you’d better have a big connection.
Double Click on the following settins and put in the numbers below – for the true / false booleans – they’ll change when you double click.
Code:
browser.tabs.showSingleWindowModePrefs – true
network.http.max-connections – 48
network.http.max-connections-per-server – 16
network.http.max-persistent-connections-per-proxy – 8
network.http.max-persistent-connections-per-server – 4
network.http.pipelining – true
network.http.pipelining.maxrequests – 100
network.http.proxy.pipelining – true
network.http.request.timeout – 300
One more thing… Right-click somewhere on that screen and add a NEW -> Integer. Name it “nglayout.initialpaint.delay” and set its value to “0”. This value is the amount of time the browser waits before it acts on information it receives. Since you’re broadband – it shouldn’t have to wait.
Now you should notice you’re loading pages MUCH faster now!
Windows®
Use registry shortcuts to disable and enable screensavers in Win XP:
The steps in this tip will show you how to edit the registry for a time-saving shortcut for enabling and disabling your screensaver.
When you perform maintenance operations such as defragmenting or backing up the hard disk, you probably disable your screensaver before you begin to prevent it from interfering with the maintenance operation. However, disabling your screensaver manually is a multistep operation that involves accessing the Display Properties dialog box, navigating to the Screen Saver tab, and setting the screen saver to None. Then, you need to re-enable the screen saver after you complete the maintenance operation.
Fortunately, you can automate the disabling and enabling screen saver procedures with a couple of registry shortcuts. Note: Editing the registry is risky, so make sure you have a verified backup before making any changes.
Here’s how.
1. Launch Notepad and type the following four lines. (Note: The second line must be blank.)
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Control Panel\Desktop]
“ScreenSaveActive”=”0″
2. Save the file to your desktop with the name Disable Screen Saver.reg.
3. Change the 0 to a 1 in the fourth line.
4. Save the file to your desktop with the name Enable Screen Saver.reg.
Now, when you need to disable the screen saver, just double-click the Disable Screen Saver.reg shortcut. To enable the screen saver, double-click the Enable Screen Saver.reg shortcut.
When you run either of these files, the Registry Editor will display two confirmation prompts—one before making the change and one after making the change.
Create a drive menu for My Computer:
Set My Computer to work like a menu for easier access to the drives you need.
By default, the My Computer item on the Start menu is configured to work like a standard folder window. If you need to access a specific drive, select My Computer from the Start menu, wait a moment for the window to appear, and then double-click the icon for the drive you need to access.
When you’re in a hurry, this two-step procedure can be time-consuming and frustrating—especially if My Computer contains a large number of drive icons. However, Windows XP makes it easy for you to configure My Computer so it works like a menu, with each drive listed as a menu item.
Here’s how.
1. Right-click the Start button, and select Properties.
2. Click Customize, which is adjacent to the Start Menu radio button, and select Advanced.
3. Scroll through the Start Menu Items list box until you see My Computer.
4. Select Display As A Menu, and click OK twice.
Now, when you select My Computer from the Start menu, you’ll see a menu of individual drives. To access the contents of that drive, just select the drive letter from the menu.
Add UNC information to the command prompt in XP:
Here’s a trick for configuring the command prompt to display the full UNC of a mapped drive letter.
If you’re like most system administrators, you more than likely prefer to perform common tasks using Windows XP’s vast array of command-line tools. If so, here’s another trick to add to your toolbox.
Did you know that you can configure the command prompt to display the full UNC of a mapped drive letter? The ability to tell at a glance which server a particular driver letter maps to can save you both time and frustration when working at the command line. All you have to do is add a special character to the Prompt command.
Here’s how.
1. Press [Windows][Break] to open the System Properties dialog box.
2. On the Advanced tab, click the Environment Variables button.
3. In the System Variables section, click the New button.
4. Enter PROMPT in the Variable Name text box.
5. Enter $m$p$g in the Variable Value text box.
6. Click OK three times to close all open dialog boxes.
Now, when you open a command prompt and access a mapped drive letter, you’ll see the UNC path in the prompt.
Switch to Windows’ basic search tool in XP:
Learn how to switch from the Windows XP Search Companion to the basic search tool.
As you probably know, the Windows XP Search Companion provides users with a lot of bells and whistles designed to make searching for files on hard drives much easier. But sometimes all of these extra features just get in the way.
If you’re longing for Windows 2000’s basic search tool, it doesn’t have to be in vain. The basic search tool is still available in Windows XP, and you can activate it with a quick registry edit. Note: Editing the registry is risky, so be sure you have a verified backup before making any changes.
Here’s how.
1. Open the Registry Editor (Regedit.exe).
2. Navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\ CurrentVersion\Explorer\CabinetState.
3. Go to Edit | New | String Value.
4. Name the new value Use Search Asst.
5. Double-click the new value, type no in the Value Data text box, and click OK.
6. Close the Registry Editor, and restart the system.
To switch back to the Search Companion, just go back to the Registry Editor, and change the Value Data to yes.
Add a Safe Mode option to the Boot menu in Windows XP:
Follow these steps to add a Safe Mode option to the Boot menu.
When you’re experiencing a problem with Windows XP, you may need to boot the system into Safe Mode more than once. However, doing so can be a tiresome process. When the Boot menu appears, you must press [F8], and then you must select Safe Mode from yet another menu.
Wouldn’t it be nice if Safe Mode were available from the Boot menu? In fact, it’s relatively easy to add a Safe Mode option to the Boot menu.
Here’s how.
1. Press [Windows][Break] to open the System Properties dialog box.
2. On the Advanced tab, click the Settings button in the Startup And Recovery section.
3. In the System Startup section, click the Edit button.
4. When the Boot.ini file opens in Notepad, locate the line that ends with the /fastdetect switch.
5. Highlight and copy that line and paste it in the line below.
6. Change the section on the line that reads WINDOWS=”Microsoft Windows XP Professional” to WINDOWS=”Safe Mode.”
7. Add the following to the end of the line:
/safeboot:minimal /sos /bootlog
Make the Windows XP Favorites menu more useful in Windows Explorer:
Your favorite menu just got better at dealing with your Favorites. This shortcut will let you cut through the maze of folders on your Windows XP machine running Windows Explorer. Note: This tip applies to both Windows XP Professional and Home.
Similar to Internet Explorer, the Favorites menu in Windows XP appears in Windows Explorer. This makes it easy for you to access the Internet from within Windows Explorer. However, it really serves no other purpose in Windows Explorer—even though it has the potential to do so much more.
You can make hard disk and network navigation much easier and more efficient if you use the Favorites menu as a place to keep shortcuts to deeply nested folders on your hard disk, as well as to network drives you access frequently. Doing so just takes a bit of rethinking about how you use and organize the Favorites menu.
Here’s how.
1. Press [Windows]R to access the Run dialog box, type Favorites in the Open text box, and click OK to open the Favorites folder in Windows Explorer.
2. Use the Make A New Folder command in the File And Folder Tasks pane to create three new folders, naming them Internet, Local Folders, and Network Folders.
3. Move all of your Internet links, except the folder titled Links, into the newly created Internet folder.
4. Navigate to some of the deeply nested folders on your hard disk that you access frequently and use the Add To Favorites command on the Favorites menu to create links in the Local Folders folder.
5. Navigate to some of the network shares that you access frequently and use the Add To Favorites command to create links in the Network Folders folder.
Now, when you’re in Windows Explorer you can use the Local Folders and Network Folders shortcuts on the Favorites menu to make quick work of your regular hard disk and network navigation.
Simplify copy and paste operations in Windows XP:
Copying and pasting in Windows XP is simple enough—but how would you like to make it even easier? Teach some old keys new tricks and simplify the copy and paste process in both Professional and Home versions.
Do you spend a lot of time on your Windows XP machine researching IT-related topics on the Internet? If so, chances are that you probably spend time copying text from interesting Web sites and then pasting that text into word processing documents for later reference. That’s four separate keyboard strokes—[Ctrl]C to copy and [Ctrl]V to paste—each time you want to save snippets of text. Wouldn’t it be nice if you could reduce each operation to a single keystroke? Well, you can!
If you have a Microsoft keyboard that provides a special set of buttons across the top, you can use the IntelliType software to reassign any of the special buttons to perform the copy and paste operations.
Here’s how.
1. Download and install the most current version of the IntelliType software for your keyboard from the Microsoft Hardware site. (This step is optional because the IntelliType software you have installed will allow you to reassign the special buttons.)
2. Access the Control Panel and double-click the Keyboard icon to display the Keyboard Properties dialog box.
3. Select the Key Settings tab, choose a key in the list, and click the Edit button to launch the Reassign A Key wizard.
4. Select the Choose From A List Of Commands option button in the Custom section and click Next.
5. In the Select A Command From The List scrolling list box, select the Copy command and click Finish.
6. Repeat steps 3 through 5 and assign another key to the Paste command.
7. When you return to the Keyboard Properties dialog box, click OK.
Now, anytime you want to perform a copy or paste operation, all you have to do is press the buttons that you reassigned. Likewise for a paste-only operation.
Windows XP System Hangs Response
Have you ever been using your computer and your system suddenly stops responding in ways like it if you try to open something it just hangs? One time I tried deleting a folder and it said it was in use, but it really wasn’t. If this ever happens to you, you can follow these simple steps to ‘reboot’ your computer without ‘rebooting’ it.
Press CRTL + ALT + DEL
Goto the ‘processes’ tab and click explorer.exe once and then click ‘end process’.
Now, click File > New Task and type explorer.exe
Everything should be fine now! If the problem is major, I would recommend actually shutting down then starting up again.
Rename Multiple Files In Winxp with ease
XP lets you rename files in bulk by simply selecting multiple files within Windows Explorer and pressing the F2 key. When you use this feature, the OS applies the name you enter to the first file and applies the same name with a number in parentheses to the other files you selected (the file extensions remain unchanged).
For example, if you select the following files,
* notes.doc
* figures.xls
* disney.jpg
* holiday.gif
and rename the first file (notes.doc) to SoD.doc, XP renames the remaining files as follows:
* SoD (1).xls
* SoD (2).jpg
* SoD(3).gif
I used to get a particular problem when i try to transfer and save the images and video clips taken by my cellphone to hard disk.Every time i tried to copy those stuff from my phone memory to my ‘cell_image’ folder, windows can not copy because already exists files with the same name. Now changing those file names to a different, is a mammoth task. This technique helped me a lot to resolve this issue. I hope, you will catch a situation too, where you can act smartly and find this tutorial useful.
Add A Url Address Bar To The Task Bar
You can add an Internet URL address bar to your Windows XP taskbar. Doing so will let you type in URLs and launch Web pages without first launching a browser. It will also let you launch some native Windows XP applications in much the same way as you would via the Run menu (so you could type in ‘calc’ without quotes to launch the calculator or ‘mspaint’ without quotes to launch Microsoft Paint. Here’s how you add the address bar:
1. Right-click on the taskbar, select Toolbars, and then click Address.
2. The word Address will appear on your taskbar.
3. Double click it to access it.
4. If that doesn’t work, your taskbar is locked. You can unlock it by right-clicking on the taskbar again and uncheck Lock the Taskbar.
NOTE: You may also need to grab the vertical dotted lines beside the word Address and drag it to the left to make the Address window appear.
Uninstall Microsft Instant Messenger
Maybe you don’t use Microstfts Instant Messenger (MSN) like many people but you will notice that it loads into memory when you fire up your operating system. It sits in the task bar stares at you. This is annoying to me at least, specially when i don’t need any service from it. Well in this kinda situation, you better choose to read on [:-D]….. This worked in WinXP, but may work on others….
So, go to START–>RUN copy and paste the following:
RunDll32 advpack.dll,LaunchINFSection %windir%\INF\msmsgs.inf,BLC.Remove
Click ok. No more msn process.
Getting older programs to run on Windows XP
Most programs run properly on Windows XP. The exceptions are some older games and other programs that were written specifically for an earlier version of Windows. To run your program on Windows XP, you can try the following, Run the Program Compatibility Wizard. As an alternative, you can set the compatibility properties manually. Update your program, drivers, or hardware. These options are covered in detail below.
————————————-
The Program Compatibility Wizard:
————————————-
This wizard prompts you to test your program in different modes (environments) and with various settings. For example, if the program was originally designed to run on Windows 95, set the compatibility mode to Windows 95 and try running your program again. If successful, the program will start in that mode each time. The wizard also allows you to try different settings, such as switching the display to 256 colors and the screen resolution to 640 x 480 pixels. If compatibility problems prevent you from installing a program on Windows XP, run the Program Compatibility Wizard on the setup file for the program. The file may be called Setup.exe or something similar, and is probably located on the Installation disc for the program. To run the Program Compatibility Wizard click Start, click Help and Support, click Find compatible hardware and software for Windows XP, and then, under See Also in the navigation pane, click “Program Compatibility Wizard.”
——————————————-
Set the compatibility properties manually:
——————————————-
As an alternative to running the Program Compatibility Wizard, you can set the compatibility properties for a program manually. The settings are the same as the options in the Program Compatibility Wizard. To set the compatibility properties for a program manually Right-click the program icon on your desktop or the shortcut on the Start menu for the program you want to run, and then click Properties. Click the Compatibility tab, and change the compatibility settings for your program.
The Compatibility tab is only available for programs installed on your hard drive. Although you can run the Program Compatibility Wizard on programs or setup files on a CD-ROM or floppy disk, your changes will not remain in effect after you close the program. For more information about an option on the Compatibility tab, right-click the option and then click “What’s This.”
———————————-
Update your program or drivers:
———————————-
If your program does not run correctly after testing it with the Program Compatibility Wizard, check the Web for updates or other fixes, as follows:
Check the Web site of the program’s manufacturer to see if an update or patch is available.
Check Windows Update to see if a fix is available for the program.
Click Home on the menu bar of Help and Support Center, then click Windows Update in the right pane.
If the program is a game that uses DirectX, ensure that you are using the latest version of DirectX. In addition, check the Web site of the manufacturer of your video card or sound card to see if newer drivers are available for either of them
Defending WinXP Pro -with what win-xp has to offer
Today I will tell you about various ways to Securing WinXP Pro with what win-xp has to offer by default. No extra third party software to tweak things which might make your system unstable and push it into the verge of reinstalling soon often.
Note: These are just notes of the changes i made to win-xp pro using win-xp options
after my default install. These changes will not secure your box 100% but they
make a good couple of 1st steps. They are in no specific order other than the
order that I performed them.
1. NTFS Partition.
2. Disable Error Reporting
3. Disable Automatic Updates (only if your XP copy is pirated)
4. Disable “Recent Documents” Viewed
5. Setup XP Firewall
6. Setup screensaver password
7. Setup BIOS password
8. Setup “AfterBios” login password
9. Account Modifications
-Rename Admin Account
-Disable Guest Account
-Disable Help_Assistant Account
-Disable Support Account
10. Install a virus scanner.
11. Change Login Screen (default shows user names)
12. Disable Remote Registry (and other services)
13. Disable/Change Auto-Search settings in IE.
—————————————————————————————–
1. NTFS Partition (I like being God over system users)
—————————————————————————————–
Be sure to install XP onto an NTFS partition so that you (the administrator) can take advantage
of file permissions. You want this option so that “you” can decide who reads, writes,
executes what files.
If you didn’t install XP onto an NTFS partition. Convert It. To convert to NTFS follow
the instructions below.
Open a command prompt and type “convert c: /FT:NTFS /v”
This command will convert your c: partition from FAT to NTFS in verbose mode.
—————————————————————————————–
2. Disable Error Reporting – we don’t want microsft to know every time we fuck up.
especially if we didn’t pay for winxp.
—————————————————————————————–
control panel >> performance and maintenance >> system >> advanced >> error reporting
(disable all)
right click “my computer” >> manage >> services and applications >> services >> ” stop
and disable” Error Reporting.
—————————————————————————————–
3. Disable automatic updates – to update, they must know what we have. thats a NO NO!
—————————————————————————————–
NOTE: DO THIS ONLY IF YOUR COPY OF XP IS PIRATED!! I suggest “auto update” if your copy
of XP is legal. If your copy is pirated then i suggest that you stay updated with
the latest fixes and patches manually.
control panel >> performance and maintenance >> system >> automatic updates
(disable updates)
right click “my computer” >> manage >> services and applications >> services >> ” stop
and disable” Automatic Updates.
—————————————————————————————–
4. Quit listing most recent documents opened under the start button – Don’t want the
girlfriend or the parents to find that interesting things you being viewing lately.
—————————————————————————————–
control panel >> appearance and themes >> task bar and start menu >> start menu >>
customize >> advanced
remove the check mark next to “List my most recently opened documents”.
—————————————————————————————–
5. Block incoming traffic to your winxp box. – Before this change, i scanned my xp box and
found it to have many ports wide open. After this change, I found nothing and xp logged
the attempts in c:\windows\pfirewall.log.
—————————————————————————————–
control panel >> network connections >> right click “local area connection” >> properties
>> advanced >> check the box under “Internet Connection Firewall” then choose “settings”.
Services Tab – leave all unchecked unless there is a service you are running that people
must be able to access.
Logging Options – Log everything.
ICMP – I left all these unchecked for the time being. (allowing nothing)
(this does not protect you from “Spy Ware”. This only stops traffic from coming into
your win-xp box (not all traffic). It does not stop traffic from going out.) If you
need to stop traffic from going out and need a more secure firewall then download a real
firewall like “zone alarm or black ice”.
—————————————————————————————–
6. Setting a screensaver password in case you leave some of your sensitive documents open when you walk away.
—————————————————————————————–
right click on the desktop >> properties >> screen saver >> check the box next to ” On
Resume, Password Protect.”
If you don’t have a password set on your user account, you can do so in control panel >>
user accounts >> change account.
—————————————————————————————–
7. Setting a BIOS password – We don’t want anyone rebooting the computer or trying to sneak
into your system while we are away at school or work.
—————————————————————————————–
I can’t explain to one how this is done due to the differences between all computers and
how the BIOS settings are entered. If you know what I am talking about then do it. If you
don’t know what I am talking about then learn how to do it. A screensaver password is useless
unless you setup a BIOS password.
——————————————————————————————
8. Setting up the “AfterBios” password. Sometimes bios passwords are easily cracked. This
password will add extra local login security in case your bios pass is cracked. I don’t
know bout you but i love having to type in 3 passwards and a username to login to my box.
——————————————————————————————
Start >> run >> type “syskey” >> choose “update” >> choose “Password Startup” >> enter a
password and choose ok.
——————————————————————————————
9. Renaming and Disabling Accounts for adminstrator, guest, help_assistant and support.
——————————————————————————————
Right click my_computer >> manage >> local users and groups
rename administrator account
disable guest account
disable help_assistant account
disable support account
——————————————————————————————-
10. Install Virus Protection…………. (We like our uncorrupted data and trojan free system)
——————————————————————————————-
Install a virus scanner. Your firewall might protect your system from unwanted hackers but
what about an unwanted virus or trojan?. I recommend installing a virus scanner such as
“Nortons” or “McAfee”.
——————————————————————————————-
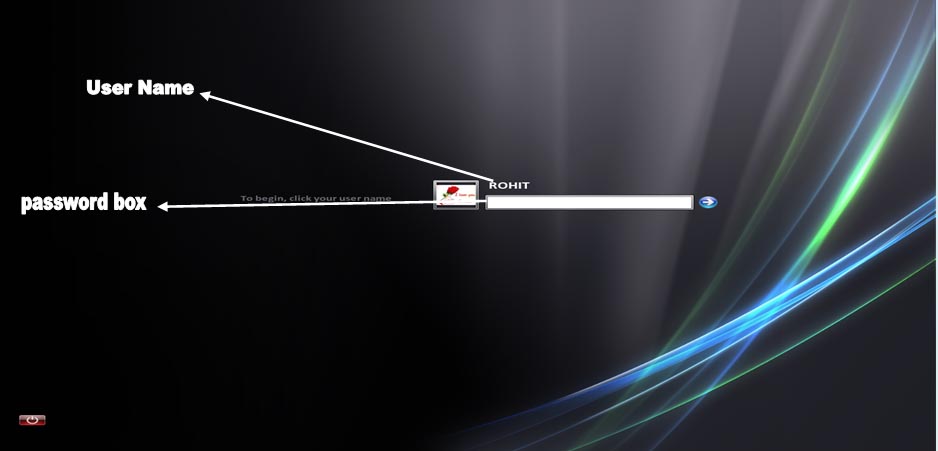
11. Change Default Login Screen………… (why do we want to share usernames with anyone?)
——————————————————————————————-
Xp uses the “welcome screen” by default. This screen has the names of all accounts on the
system so that the user only has to click on their name and type a password. Come on now….
We aren’t that damn lazy. If we change this screen to the normal login, then prying eyes
will have to know a username and password to get in. Follow the instruction below to change
this.
control panel >> user accounts >> change the way users log on or off
uncheck the box next to “Use Welcome Screen” and choose “apply options”.
——————————————————————————————-
12. Disable Remote Registry……….(why would I need to edit my registry remotely anyway?)
——————————————————————————————-
right click “my computer” >> manage >> services and applications >> services >> ” stop
and disable” Remote Registry.
NOTE: disable any services running in this area that you aren’t using.
——————————————————————————————-
13. Disable/Change Auto-search in Internet Explorer. This is not really a security risk but it
is important to some people that prefer to keep their internet surfing to themselves and
away from microsoft.
——————————————————————————————-
Open Internet Explorer >> Click the “search” button >> click the “customize” button >> click
“autosearch settings” >> FOLLOW INSTRUCTIONS BELOW………..
DISABLE: In the “When Searching” drop down menu, select “Do not search from the address bar”.
>> click “ok” >> “ok”. Type an invalid address in your address bar and see if it
takes you to the msn search page or if it gives a “page not found” error. In this
case, the “page not found” error is what we want.
CHANGE: If you wish not to disable, but you wish to change it to your favorite “google.com”
search page. Instead of following the “DISABLE” instructions, follow the instructions
below. Choose “Google Sites (or whatever you prefer)” from the “choose a search provider
to search from address bar” drop down menu >> click “ok” >> “ok”
If you are running Windows XP Professional on your computer you can install Microsoft’s web server, Internet Information Server 5.1 (IIS) for free from the Windows XP Pro installation CD and configure it to run on your system by following the instructions below: –
1. Place the Windows XP Professional CD-Rom into your CD-Rom Drive.
2. Open ‘Add/Remove Windows Components’ found in ‘Add/Remove Programs’ in the ‘Control Panel’.
3. Place a tick in the check box for ‘Internet Information Services (IIS)’ leaving all the default installation settings intact.
4. Once IIS is installed on your machine you can view your home page in a web browser by typing ‘http://localhost’ (you can substitute ‘localhost’ for the name of your computer) into the address bar of your web browser. If you have not placed your web site into the default directory you should now be looking at the IIS documentation.
5. If you are not sure of the name of your computer right-click on the ‘My Computer’ icon on your desktop, select ‘Properties’ from the shortcut menu, and click on the ‘Computer Name’ tab.
6. Your default web directory to place your web site in is ‘C:\Inetpub\wwwroot’, but if you don’t want to over write the IIS documentation found in this directory you can set up your own virtual directory through the ‘Internet Information Services’ console.
7. The ‘Internet Information Services’ console can be found in the ‘Administration Tools’ in the ‘Control Panel’ under ‘Performance and Maintenance’, if you do not have the control panel in Classic View.
8. Double-click on the ‘Internet Information Services’ icon.
9. Once the ‘Internet Information Services’ console is open you will see any IIS web services you have running on your machine including the SMTP server and FTP server, if you chose to install them with IIS.
10. To add a new virtual directory right click on ‘Default Web Site’ and select ‘New’, followed by ‘Virtual Directory’, from the drop down list.
You can lock your XP workstation with two clicks of the mouse.
1. Create a new shortcut on your desktop using a right mouse click.
2. Enter ‘rundll32.exe user32.dll, LockWorkStation’ in the location field.
3. Give the shortcut a name you like.
That’s it — just double click on it and your computer will be locked. And if that’s not easy enough, Windows key + L will do the same.
How to fix corrupted files in XP
This tutorial has been made so people that are having problems with corrupted files, can learn how to fix them easy.
Required:
1. Windows XP operating system
2. Windows XP cd
Now, follow this steps:
1. Place the xp cd in your cd/dvd drive
2. Go to start
3. run
4. type in ‘sfc /scannow’ (without the ‘)
Now it should all load, and fix all your corrupted file on win XP.
How To Convert File System, fat – fat32 to ntfs
open a dos prompt and give the command
convert d: /fs:ntfs
this command would convert your d: drive to ntfs.
if the system cannot lock the drive, you will be prompted to convert it during next reboot.
Normally you should select yes.
Conversion from fat/fat32 to ntfs is non-destructive, your data on the drive will NOT be lost.
Be aware that converting to ntfs will make that partition of your
drive unreadable under dos unless you have ntfs utilites to do so.
How to burn quicker in win xp
WIN XP has burning software built in, which can cause problems sometimes when burning with other programs.
So you can turn windows xp burning tool off like this.
1. Go to “administrative tools” in the control panel.
2. In the “services” list, disable the IMAPI CD-Burning COM service.
Enjoy!!!!!!!
How Do U See Hidden Files, Using DOS…
Here is a Simple and useful tip:
***************************
at command prompt just type
dir /ah
if the list is too long u can use
dir /ah/p/w
***************************
How To Access Your Folders From Your Taskbar
This is an easy way to get to the folders on your system without having to open a Windows Explorer Window every time you want to access files. I find it very useful to have this feature as it allows me to access my Folders and Drives immediately and saves me a lot of time.
This works in Windows XP:
1. Right Click an empty spot on your Taskbar (Between your Start Button and your System Tray).
2. Click Toolbars.
3. Click New Toolbar.
4. A Small Window will Open that allows you to pick the folder you wish to make a Toolbar. If you want to access your Desktop Without having to minimize all your windows. Just Pick Desktop. If you want to access ONLY your My Documents Folder, Select that. Any folder will work for this.
5. Click OK.
The New Tool bar will appear at the bottom of your screen next to your System Tray.
If you find this to be not useful, Repeat Steps 1 and 2 and then check click the Toolbar you created that has a check mark next to it. And it will disappear.
Delete Files From The Recent File List In Windows
This tip requires a change to the Windows Registry. Please see the MSFN Guide “Backup Your Registry” if you are new to the Windows Registry.
Windows Media Player (WMP) is a built-in application that allows you to play multimedia files. Like many other applications, WMP remembers the most recently played files and displays them in the Recent File List under the File menu. This feature is useful if you regularly play certain files, but you may want to clear the list if you share the computer and a user account or create archives and CDs.
There are two ways you can clear the list:
I. The ClearMRU.exe Utility is available for free in the Windows Media Player Bonus Pack from Microsoft, but Microsoft does not support this tool.
II. You can also manually delete the list through the Windows Registry:
1. Start the Windows Registry Editor, regedit.exe, by typing regedit in the Windows Run Command Line.
2. Go to HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Player\RecentFileList.
3. Delete the RecentFileList subkey.
4. If you’ve also streamed content from the Internet, you can delete the RecentURLList subkey.
5. Exit the Registry Editor.
6. Restart the computer.
To keep certain files in the list, don’t delete the entire key. Deleting individual entries within the key will get rid of the files that you no longer want in the Recent File List.
——————
Another method:
——————
1. Fire up Windows Media player by Start-> All Programs-> Windows Media player
2. Now go to Tools->Options->Privacy
3. Look for the Button “Clear History”
4. Apply->ok
So Keep rocking with your muzik! ! ! ! ! ! ! ! !
Data Capacity of CDs
Abstract
You can fit on a S/VCD without overburning:
– approx. 735 MB of MPEG data onto a 74min/650MB disc
– approx. 795 MB of MPEG data onto an 80min/700MB disc
You can fit on a CD-ROM without overburning:
– approx. 650 MB of data onto a 74min/650MB disc
– approx. 703 MB of data onto an 80min/700MB disc
—————————————————————-
VCD stands for ‘Video Compact Disc’ and basically it is a CD that contains moving pictures and sound. If you’re familiar with regular audio/music CDs, then you will know what a VCD looks like. A VCD has the capacity to hold up to 74/80 minutes on 650MB/700MB CDs respectively of full-motion video along with quality stereo sound. VCDs use a compression standard called MPEG to store the video and audio. A VCD can be played on almost all standalone DVD Players and of course on all computers with a DVD-ROM or CD-ROM drive with the help of a software based decoder / player.
SVCD stands for “Super VideoCD”. A SVCD is very similiar to a VCD,it has the capacity to hold about 35-60 minutes on 74/80 min CDs of very good quality full-motion video along with up to 2 stereo audio tracks and also 4 selectable subtitles. A SVCD can be played on many standalone DVD Players and of course on all computers with a DVD-ROM or CD-ROM drive with the help of a software based decoder / player. It is also possible to use menus and chapters, similiar to DVDs, on a SVCD and also simple photo album/slide shows with background audio. The quality of a SVCD is much better than a VCD, especially much more sharpen picture than a VCD because of the higher resolution. But the quality depends how many minutes you choose to store on a CD, less minutes/CD generally means higher quality.
—————————————————————-
Introduction
Let us ignore for now the terms of megabyte for CD capacity and try to understand how the data is stored on a CD.
As well all know, the data is stored digitally as binary data. This means, however the actual information is actually kept on the disc, this information is in the form of “1”s and “0”s. Physically, the information on a CD is as pits on a thin sheet of metal (aluminium).
An a CD-R disc, the data is physically on an organic dye layer which simulates the metal layer on a real pressed CD.
—————————————————————-
How is the information structured
Now, on the CD, the information isn’t just organised from beginning to end willy-nilly. Otherwise, it would be really hard to find a useful piece of information on the CD.
Rather, the information is organised in sectors. Consider a sector as like a page in a book. Just like you are able to quickly find something in a book if you know the page number, you can quickly find something on a CD if you know the sector number.
Now, remember that the CD was original made to hold audio data. It was decided, that the CD would would 75 sectors per second of audio. Although I cannot guess where this number comes from, it is quite appropriate for the audio CD. It means that you can “seek” an audio CD accurately to 1/75th of a second — which is more than enough for consumer purposes.
Now, with this in mind, we can work out the total data capacity of user data for 1 sector.
—————————————————————-
The total data capacity of user data of 1 sector on a CD
CD audio uses uncompressed PCM stereo audio, 16-bit resolution sampled at 44.1 kHz.
Thus 1 second of audio contains:
16 bits/channel * 2 channels * 44100 samples/second * 1 second
= 1411200 bits
= 176400 bytes
Since there are 75 sectors per second
1 sector
= 176400 bytes / 75
= 2352 bytes
One sector on a CD contains 2352 bytes max.
—————————————————————-
The concept of different MODES and FORMS of burning
Now, audio CD was well and good, but the medium would become much more useful if you could store other data on the disc as well. This became to be know as CD-ROM of course.
Now, the audio-CD uses the ENTIRE sector for audio data.
However, for CD-ROMs this caused a problem. Simply, CDs and the CD reading mechanisms were not 100% faultless. That is, errors (indeed frequent errors) could be made during the reading. For audio CDs, this does not matter as much as you could simply interpolate from the adjacent audio samples. This will obviously NOT DO for data CDs. A single bit error could lead to a program being unexecutable or ruin an achive file.
Thus, for CD-ROMs, part of each sector is devoted to error correction codes and error detection codes. The CD-R FAQ has the details, but in effect, only 2048 bytes out of a total of 2352 bytes in each sector is available for user data on a data CD.
This burning mode is either MODE1 or MODE2 Form1.
—————————————————————-
MODE2 Form2 sectors of VCDs and SVCDs
Now, for VCDs and SVCDs, the video tracks do not necessarily require the robust error correction as normal data on a CD-ROM. However, there is still some overhead per sector that is used for something other than video data (e.g., sync headers).
S/VCDs video tracks are burnt in what is called MODE2 Form2 sectors. In this mode, only 2324 bytes out of a total of 2352 bytes in each sector is available for user data.
This is MUCH MORE than for CD-ROMs, but still less per sector than audio CD.
—————————————————————-
The disc capacities of CD-ROMs, audio-CDs and VCDs
Now, obviously what ultimately determines the capacity of a disc is the total number of sectors it contains. This is similar to the total number of pages in a blank exercise book (if you recall the book analogy).
The secondary determinant is the burning mode of the disc.
For audio CDs, it is as if you could fill each page from top to bottom with audio data as the entire sector is used for audio data.
For CD-ROMs, it is as if you need to first rule a margin and then leave the bottom part of each page for footnotes (headers + ECC + EDC). The amount of text you can actually write per page is then less due to these other constraints.
For S/VCDs, we still need to rule a margin on the page, but we don’t have to worry about the footnotes (headers). We can fit MORE text than a CD-ROM, but less than an audio-CD.
Now remember, 1 second on a CD = 75 sectors.
Thus:
– 74 min CD = 333,000 sectors
– 80 min CD = 360,000 sectors
Data capacity in Mb for an audio-CD
74 min
= 333,000 sectors * 2352 bytes / sector
= 783216000 bytes
= 746.9 Mb
80 min
= 360,000 sectors * 2352 bytes / sector
= 846720000 bytes
= 807.5 Mb
Data capacity in Mb for a CD-ROM
74 min
= 333,000 sectors * 2048 bytes / sector
= 681984000 bytes
= 650.4 Mb
80 min
= 360,000 sectors * 2048 bytes / sector
= 737280000 bytes
= 703.1 Mb
Data capacity in Mb for a S/VCD
74 min
= 333,000 sectors * 2324 bytes / sector
= 773892000 bytes
= 738.0 Mb
80 min
= 360,000 sectors * 2324 bytes / sector
= 836640000 bytes
= 797.9 Mb
—————————————————————-
Conclusions
As you can see, the often quoted capacities of 650MB and 700MB refer to CD-ROM capacities.
Due to the fact that S/VCDs use a different burning mode where MORE of each sector is available as user data, the relatively capacities are HIGHER.
Now, since S/VCDs are not composed of PURELY video tracks and have some unavoidable overheads, the actually total capacity left for video tracks is a few Mb less for each disc (about 735 Mb for 74min discs and 795 Mb for 80min discs). This is where the often quoted capacities of 740MB and 800MB come from. They are quite accurate.
All these capacities are available BEFORE overburning. Overburning is where you burn MORE sectors than the disc is rated for. If you overburn, you can typically achieve about 1-2 minutes of additional capacity (depending on your drive and media).
Delete An Undeletable File
Open a Command Prompt window and leave it open.
Close all open programs.
Click Start, Run and enter TASKMGR.EXE
Go to the Processes tab and End Process on Explorer.exe.
Leave Task Manager open.
Go back to the Command Prompt window and change to the directory the AVI (or other undeletable file) is located in.
At the command prompt type DEL where is the file you wish to delete.
Go back to Task Manager, click File, New Task and enter EXPLORER.EXE to restart the GUI shell.
Close Task Manager.
Or you can try this
Open Notepad.exe
Click File>Save As..>
locate the folder where ur undeletable file is
Choose ‘All files’ from the file type box
click once on the file u wanna delete so its name appears in the ‘filename’ box
put a ” at the start and end of the filename
(the filename should have the extension of the undeletable file so it will overwrite it)
click save,
It should ask u to overwrite the existing file, choose yes and u can delete it as normal
Here’s a manual way of doing it. I’ll take this off once you put into your first post zain.
1. Start
2. Run
3. Type: command
4. To move into a directory type: cd c:\*** (The stars stand for your folder)
5. If you cannot access the folder because it has spaces for example Program Files or Kazaa Lite folder you have to do the following. instead of typing in the full folder name only take the first 6 letters then put a ~ and then 1 without spaces. Example: cd c:\progra~1\kazaal~1
6. Once your in the folder the non-deletable file it in type in dir – a list will come up with everything inside.
7. Now to delete the file type in del ***.bmp, txt, jpg, avi, etc… And if the file name has spaces you would use the special 1st 6 letters followed by a ~ and a 1 rule. Example: if your file name was bad file.bmp you would type once in the specific folder thorugh command, del badfil~1.bmp and your file should be gone. Make sure to type in the correct extension.
Disable The Send Error Report, to Microsuft
To disable the stupid feature in WinXP which tries to send a report to microsuft every time a program crashes you will have to do this:
——————————————————————————–
1. Open Control Panel
2. Click on Preformance and Maintenance.
3. Click on System.
4. Then click on the Advanced tab
5. Click on the error reporting button on the bottom of the windows.
6. Select Disable error reporting.
7. Click OK
8. Click OK
——————————————————————————–
Find Stuff using CTRL-F
Has this ever happened to you?
You’re looking for something on a long web page with Internet Explorer or Netscape. You think it’s there, but you’re faced with seemingly insurmountable number of paragraphs, sentences, and words to hunt though.
Well, next time this happens to you, hit the Edit menu, Find (or CTRL-F for you shortcut lovers). You’ll get a handy little “find” box that lets you type in a specific word. After you type in your search term, hit the Find Next button and Explorer will look for that word on the page. If it’s successful, you’ll be zapped right to it.
As if that wasn’t cool enough, you can also use a variation of this tip in Windows Explorer. Next time you’re looking for a file in Explorer, hit CRTL-F and you’ll get a Find or Search box (depending on what flavor of Windows you’re using).
If you are already in the area of your hard drive where you think the file is (say, My Documents), hit CTRL-F and your search will be set to look in the My Documents folder.
Internet
If you wanna remove those nasty ads from the pages which waste lot of time and bandwidth then here is something for you I believe it will help you a lot.
How it works:
It’s possible to set up a name server as authoritative for any domain you choose, allowing you to specify the DNS records for that domain. You can also configure most computers to be sort of mini-nameservers for themselves, so that they check their own DNS records before asking a nameserver. Either way, you get to say what hostname points to what IP address. If you haven’t guessed already, the way you block ads it to provide bogus information about the domains we don’t want to see – ie, all those servers out there that dedicate their existence to spewing out banner ads.
The hosts file
Probably the most common way people block ads like this is with something called the “hosts file”. The hosts file is a simple list of hostnames and their corresponding IP addresses, which your computer looks at every time you try and contact a previously unknown hostname. If it finds an entry for the computer you’re trying to reach, it sets the IP address for that computer to be what ever’s in the hosts file.
127.0.0.1 is a special IP address which, to a computer, always means that computer. Any time a machine sends a network request to 127.0.0.1, it is talking to itself. This is very useful when it comes to blocking ads, because all we have to do is specify the IP address of any ad server to be 127.0.0.1. And to do that, all we have to do is edit the hosts file. What will happen then is something like this:
1. you visit a web page
2. the web page contains a banner ad stored on the server “ads.example.com”
3. your computer says “ads.example.com? never heard of it. wait a second, let’s see if I’ve got the number on me…”
4. your computer finds its hosts file and checks to see if ads.example.com is listed
5. it finds the hostname, which points to 127.0.0.1
6. “great”, says the computer, and sends off a request to 127.0.0.1 for the banner ad that’s supposed to be on the page
7. “oh”, says the computer, and fails to show anything because it just sent a request to itself for a banner ad
Where’s my hosts file?
* Windows 95 / 98 / ME: C:\Windows (I think)
* Windows NT: C:\WinNT\hosts
* Windows 2000: C:\WinNT\system32\drivers\etc\
* Windows XP: C:\Windows\System32\drivers\etc
* FreeBSD / Linux / Mac OS X / Unix operating systems: /etc/hosts
The format of the hosts file is very simple – IP address, whitespace, then a list of hostnames (except for older Macs; please see above). However, you don’t need to know anything about the format if you don’t want to as you can just view the list hosts file.
Of course, that’s not the only way to use the list, but it’s probably the most simple for most people.
A simple tool to find music on the net
Exploseek is a nice simple tool to find music on the net. It is possible to use the major search engines to type your queries, but if you use this tool it will be much easier as some of you have probably seen already. We always try to improve the queries, if possible, and will update it at random times. Further you don’t need to install a peer-to-peer program with possible spyware and other security issues, the price to pay is that you will not always find as much as such a program, but on a lucky day you find a load of music.
Useful information on Internet Merchant Account
Choosing An Internet Merchant Account:
Surf to Google and perform a search on “Internet Merchant Account”. The results are staggering (2,300,000 results!) If you have created a web based business and need to accept credit card payments, your choices are limitless. Before you partner with a provider, take time to understand the different components of Internet credit card processing, and know what to look for in a merchant provider.
How It Works:
Accepting credit card payments through your web site actually requires multiple components. Between a paying customer and your bank account, three layers exist:
Payment Gateway – This is the code that will transmit a customer’s order to and from an Internet merchant account provider. The payment gateway provides you the ability to accept customer billing information (credit card number, credit card type, expiration date, and payment amount) and the necessary validation steps that must be followed before the credit card is actually billed.
Internet Merchant Account – A Merchant Account is an account with a financial institution or bank, which enables you to accept credit card payments from your clients. The payment gateway actually transmits the billing information to the Internet merchant account provider. Unfortunately, most local banks do not provide Internet merchant account capability.
The main reason why most local financial institutions or banks do not want to provide online merchant accounts is because transactions conducted over the Internet are totally different from face to face transactions where a signature is required to authorize the purchase. This makes online transactions prone to credit card fraud. Fraud protection should be one of your primary considerations when choosing an Internet merchant account provider.
Web Site – Regardless of which merchant provider and gateway service you choose, your web site will need to integrate with your service providers. Most providers include detailed web integration instructions.
How Much Does It Cost ?
Understanding the total costs of your merchant provider can be tricky. Remember my Google example – there are more merchant account providers than there are people looking for internet merchant accounts so ask questions and be picky! Typically, an internet merchant account will have three types of costs:
– Up Front Application Fees
– On Going Fixed Fee
– Discount Rate
– Fixed Transaction Fee
– Termination Fees
– Miscellaneous Fees
Let us discuss each type of cost:
* Up Front Application Fees
Many Internet merchant accounts will require an up front application fee. This fee, supposedly, is to cover their costs for processing your application. In case you choose not to open an Internet merchant account, they still cover their initial costs. Although common, many providers waive these fees and I recommend that you choose a provider that does not require an up front fee.
* On Going Fixed Fee
Most all Internet merchant providers require a monthly fixed fee or “statement fee” as it is commonly named, which is simply another way to cover their costs and make money. You will be hard pressed to find a provider that does not require this type of fee on a monthly basis. However, do not choose an Internet merchant account that requires more than $10 per month. Additionally, most Internet merchant providers require a monthly minimum (usually $25). The bottom line is that you will be paying at least $25 per month (on top of the monthly statement fee) for your account.
* Discount Rate
Usually, the discount rate will be between 2 and 4 percent. The discount rate is the sales commission the provider earns on each sale. For example, if the discount rate offered is 3%, and you receive a sale over your web site for $20, you will owe 60 cents to your Internet merchant provider.
* Fixed Transaction Fee
Usually between $0.20 and $0.30, the fixed transaction fee is the fixed fee portion of each sale. Unlike the discount rate, the fixed transaction fee is the same for every transaction. Whether you get a $1 sale or a $100 sale, the transaction fee will be the same.
* Termination Fee
A bit more hidden in the small print, a termination fee can apply if you cancel your merchant account within a specified period of time (usually within one year). But beware, some merchant providers require a three year commitment!
* Miscellaneous Fees
If a customer requests a refund and they want their credit card credited, an Internet merchant provider will charge you a separate fee (usually between $10 – $20). Read the contract carefully, as other special fees may apply.
Putting It All Together
Now that the different fees have been explained, let us look at an example set of transactions to help understand what an Internet merchant account may cost your business on a monthly basis.
I have created a simple formula to help you calculate your monthly charges:
Total Charges = Statement Fee + Number of Transactions x (Average Sale x Discount Rate + Fixed Transaction Fee) + (Number of Charge backs x Charge back Fee)
For example, let us see you sell widgets over the Internet. The sales price for each widget is $10. You typically have 100 sales per month and about 5 people request refunds (charge backs). For this example, let us assume you have signed up with Jones&Jones Internet merchant account services and have the following terms:
Discount Rate – %2.5
Statement Fee – $10
Fixed Transaction Fee – $0.30
Charge back Fee – $15
Using my formula above, your monthly Jones&Jones charges will be:
Total Charges = 10 + 100 x (10 x .025 + 0.3) + (5 x 15) = $140
You can calculate your monthly sales revenue by multiplying your sales volume by your price:
Monthly Sales Revenue = 100 x $10 = $1000
Your Internet merchant provider is costing you 14% of your total sales.
Making Your Decision
Before you choose and Internet merchant provider, understand all of the cost components. Use your current or projected sales data to forecast what your Internet merchant account costs will be. Planning ahead can save you time and money.
I hope this insight will provide a good use for those who want to do business on the web.
Evolution Of Computer Viruses History Of Viruses
part 1:
Like any other field in computer science, viruses have evolved -a great deal indeed- over the years. In the series of press releases which start today, we will look at the origins and evolution of malicious code since it first appeared up to the present.
Going back to the origin of viruses, it was in 1949 that Mathematician John Von Neumann described self-replicating programs which could resemble computer viruses as they are known today. However, it was not until the 60s that we find the predecessor of current viruses. In that decade, a group of programmers developed a game called Core Wars, which could reproduce every time it was run, and even saturate the memory of other players’ computers. The creators of this peculiar game also created the first antivirus, an application named Reeper, which could destroy copies created by Core Wars.
However, it was only in 1983 that one of these programmers announced the existence of Core Wars, which was described the following year in a prestigious scientific magazine: this was actually the starting point of what we call computer viruses today.
At that time, a still young MS-DOS was starting to become the preeminent operating system worldwide. This was a system with great prospects, but still many deficiencies as well, which arose from software developments and the lack of many hardware elements known today. Even like this, this new operating system became the target of a virus in 1986: Brain, a malicious code created in Pakistan which infected boot sectors of disks so that their contents could not be accessed. That year also saw the birth of the first Trojan: an application called PC-Write.
Shortly after, virus writers realized that infecting files could be even more harmful to systems. In 1987, a virus called Suriv-02 appeared, which infected COM files and opened the door to the infamous viruses Jerusalem or Viernes 13. However, the worst was still to come: 1988 set the date when the “Morris worm” appeared, infecting 6,000 computers.
From that date up to 1995 the types of malicious codes that are known today started being developed: the first macro viruses appeared, polymorphic viruses … Some of these even triggered epidemics, such as MichaelAngelo. However, there was an event that changed the virus scenario worldwide: the massive use of the Internet and e-mail. Little by little, viruses started adapting to this new situation until the appearance, in 1999, of Melissa, the first malicious code to cause a worldwide epidemic, opening a new era for computer viruses.
part 2:
This second installment of ‘The evolution of viruses’ will look at how malicious code used to spread before use of the Internet and e-mail became as commonplace as it is today, and the main objectives of the creators of those earlier viruses.
Until the worldwide web and e-mail were adopted as a standard means of communication the world over, the main mediums through which viruses spread were floppy disks, removable drives, CDs, etc., containing files that were already infected or with the virus code in an executable boot sector.
When a virus entered a system it could go memory resident, infecting other files as they were opened, or it could start to reproduce immediately, also infecting other files on the system. The virus code could also be triggered by a certain event, for example when the system clock reached a certain date or time. In this case, the virus creator would calculate the time necessary for the virus to spread and then set a date –often with some particular significance- for the virus to activate. In this way, the virus would have an incubation period during which it didn’t visibly affect computers, but just spread from one system to another waiting for ‘D-day’ to launch its payload. This incubation period would be vital to the virus successfully infecting as many computers as possible.
One classic example of a destructive virus that lay low before releasing its payload was CIH, also known as Chernobyl. The most damaging version of this malicious code activated on April 26, when it would try to overwrite the flash-BIOS, the memory which includes the code needed to control PC devices. This virus, which first appeared in June 1998, had a serious impact for over two years and still continues to infect computers today.
Because of the way in which they propagate, these viruses spread very slowly, especially in comparison to the speed of today’s malicious code. Towards the end of the Eighties, for example, the Friday 13th (or Jerusalem) virus needed a long time to actually spread and continued to infect computers for some years. In contrast, experts reckon that in January 2003, SQLSlammer took just ten minutes to cause global communication problems across the Internet.
Notoriety versus stealth
For the most part, in the past, the activation of a malicious code triggered a series of on screen messages or images, or caused sounds to be emitted to catch the user’s attention. Such was the case with the Ping Pong virus, which displayed a ball bouncing from one side of the screen to another. This kind of elaborate display was used by the creator of the virus to gain as much notoriety as possible. Nowadays however, the opposite is the norm, with virus authors trying to make malicious code as discreet as possible, infecting users’ systems without them noticing that anything is amiss.
part 3:
This third installment of ‘The evolution of viruses’ will look at how the Internet and e-mail changed the propagation techniques used by computer viruses.
Internet and e-mail revolutionized communications. However, as expected, virus creators didn’t take long to realize that along with this new means of communication, an excellent way of spreading their creations far and wide had also dawned. Therefore, they quickly changed their aim from infecting a few computers while drawing as much attention to themselves as possible, to damaging as many computers as possible, as quickly as possible. This change in strategy resulted in the first global virus epidemic, which was caused by the Melissa worm.
With the appearance of Melissa, the economic impact of a virus started to become an issue. As a result, users -above all companies- started to become seriously concerned about the consequences of viruses on the security of their computers. This is how users discovered antivirus programs, which started to be installed widely. However, this also brought about a new challenge for virus writers, how to slip past this protection and how to persuade users to run infected files.
The answer to which of these virus strategies was the most effective came in the form of a new worm: Love Letter, which used a simple but effective ruse that could be considered an early type of social engineering. This strategy involves inserting false messages that trick users into thinking that the message includes anything, except a virus. This worm’s bait was simple; it led users to believe that they had received a love letter.
This technique is still the most widely used. However, it is closely followed by another tactic that has been the center of attention lately: exploiting vulnerabilities in commonly used software. This strategy offers a range of possibilities depending on the security hole exploited. The first malicious code to use this method –and quite successfully- were the BubbleBoy and Kakworm worms. These worms exploited a vulnerability in Internet Explorer by inserting HTML code in the body of the e-mail message, which allowed them to run automatically, without needing the user to do a thing.
Vulnerabilities allow many different types of actions to be carried out. For example, they allow viruses to be dropped on computers directly from the Internet -such as the Blaster worm-. In fact, the effects of the virus depend on the vulnerability that the virus author tries to exploit.
part 4:
In the early days of computers, there were relatively few PCs likely to contain “sensitive” information, such as credit card numbers or other financial data, and these were generally limited to large companies that had already incorporated computers into working processes.
In any event, information stored in computers was not likely to be compromised, unless the computer was connected to a network through which the information could be transmitted. Of course, there were exceptions to this and there were cases in which hackers perpetrated frauds using data stored in IT systems. However, this was achieved through typical hacking activities, with no viruses involved.
The advent of the Internet however caused virus creators to change their objectives, and, from that moment on, they tried to infect as many computers as possible in the shortest time. Also, the introduction of Internet services -like e-banking or online shopping- brought in another change. Some virus creators started writing malicious codes not to infect computers, but, to steal confidential data associated to those services. Evidently, to achieve this, they needed viruses that could infect many computers silently.
Their malicious labor was finally rewarded with the appearance, in 1986, of a new breed of malicious code generically called “Trojan Horse”, or simply “Trojan”. This first Trojan was called PC-Write and tried to pass itself off as the shareware version of a text processor. When run, the Trojan displayed a functional text processor on screen. The problem was that, while the user wrote, PC-Write deleted and corrupted files on the computers’ hard disk.
After PC-Write, this type of malicious code evolved very quickly to reach the stage of present-day Trojans. Today, many of the people who design Trojans to steal data cannot be considered virus writers but simply thieves who, instead of using blowtorches or dynamite have turned to viruses to commit their crimes. Ldpinch.W or the Bancos or Tolger families of Trojans are examples of this
part 5:
Even though none of them can be left aside, some particular fields of computer science have played a more determinant role than others with regard to the evolution of viruses. One of the most influential fields has been the development of programming languages.
These languages are basically a means of communication with computers in order to tell them what to do. Even though each of them has its own specific development and formulation rules, computers in fact understand only one language called “machine code”.
Programming languages act as an interpreter between the programmer and the computer. Obviously, the more directly you can communicate with the computer, the better it will understand you, and more complex actions you can ask it to perform.
According to this, programming languages can be divided into “low and high level” languages, depending on whether their syntax is more understandable for programmers or for computers. A “high level” language uses expressions that are easily understandable for most programmers, but not so much for computers. Visual Basic and C are good examples of this type of language.
On the contrary, expressions used by “low level” languages are closer to machine code, but are very difficult to understand for someone who has not been involved in the programming process. One of the most powerful, most widely used examples of this type of language is “assembler”.
In order to explain the use of programming languages through virus history, it is necessary to refer to hardware evolution. It is not difficult to understand that an old 8-bit processor does not have the power of modern 64-bit processors, and this of course, has had an impact on the programming languages used.
In this and the next installments of this series, we will look at the different programming languages used by virus creators through computer history:
– Virus antecessors: Core Wars
As was already explained in the first chapter of this series, a group of programs called Core Wars, developed by engineers at an important telecommunications company, are considered the antecessors of current-day viruses. Computer science was still in the early stages and programming languages had hardly developed. For this reason, authors of these proto-viruses used a language that was almost equal to machine code to program them.
Curiously enough, it seems that one of the Core Wars programmers was Robert Thomas Morris, whose son programmed -years later- the “Morris worm”. This malicious code became extraordinarily famous since it managed to infect 6,000 computers, an impressive figure for 1988.
– The new gurus of the 8-bits and the assembler language.
The names Altair, IMSAI and Apple in USA and Sinclair, Atari and Commodore in Europe, bring memories of times gone by, when a new generation of computer enthusiasts “fought” to establish their place in the programming world. To be the best, programmers needed to have profound knowledge of machine code and assembler, as interpreters of high-level languages used too much run time. BASIC, for example, was a relatively easy to learn language which allowed users to develop programs simply and quickly. It had however, many limitations.
This caused the appearance of two groups of programmers: those who used assembler and those who turned to high-level languages (BASIC and PASCAL, mainly).
Computer aficionados of the time enjoyed themselves more by programming useful software than malware. However, 1981 saw the birth of what can be considered the first 8-bit virus. Its name was “Elk Cloner”, and was programmed in machine code. This virus could infect Apple II systems and displayed a message when it infected a computer.
part 6:
Computer viruses evolve in much the same way as in other areas of IT. Two of the most important factors in understanding how viruses have reached their current level are the development of programming languages and the appearance of increasingly powerful hardware.
In 1981, almost at the same time as Elk Kloner (the first virus for 8-bit processors) made its appearance, a new operating system was growing in popularity. Its full name was Microsoft Disk Operating System, although computer buffs throughout the world would soon refer to it simply as DOS.
DOS viruses
The development of MS DOS systems occurred in parallel to the appearance of new, more powerful hardware. Personal computers were gradually establishing themselves as tools that people could use in their everyday lives, and the result was that the number of PCs users grew substantially. Perhaps inevitably, more users also started creating viruses. Gradually, we witnessed the appearance of the first viruses and Trojans for DOS, written in assembler language and demonstrating a degree of skill on the part of their authors.
Far less programmers know assembler language than are familiar with high-level languages that are far easier to learn. Malicious code written in Fortran, Basic, Cobol, C or Pascal soon began to appear. The last two languages, which are well established and very powerful, are the most widely used, particularly in their TurboC and Turbo Pascal versions. This ultimately led to the appearance of “virus families”: that is, viruses that are followed by a vast number of related viruses which are slightly modified forms of the original code.
Other users took the less ‘artistic’ approach of creating destructive viruses that did not require any great knowledge of programming. As a result, batch processing file viruses or BAT viruses began to appear.
Win16 viruses
The development of 16-bit processors led to a new era in computing. The first consequence was the birth of Windows, which, at the time, was just an application to make it easier to handle DOS using a graphic interface.
The structure of Windows 3.xx files is rather difficult to understand, and the assembler language code is very complicated, as a result of which few programmers initially attempted to develop viruses for this platform. But this problem was soon solved thanks to the development of programming tools for high-level languages, above all Visual Basic. This application is so effective that many virus creators adopted it as their ‘daily working tool’. This meant that writing a virus had become a very straightforward task, and viruses soon appeared in their hundreds. This development was accompanied by the appearance of the first Trojans able to steal passwords. As a result, more than 500 variants of the AOL Trojan family -designed to steal personal information from infected computers- were identified.
part 7:
This seventh edition on the history of computer viruses will look at how the development of Windows and Visual Basic has influenced the evolution of viruses, as with the development of these, worldwide epidemics also evolved such as the first one caused by Melissa in 1999.
While Windows changed from being an application designed to make DOS easier to manage to a 32-bit platform and operating system in its own right, virus creators went back to using assembler as the main language for programming viruses.
Versions 5 and 6 of Visual Basic (VB) were developed, making it the preferred tool, along with Borland Delphi (the Pascal development for the Windows environment), for Trojan and worm writers. Then, Visual C, a powerful environment developed in C for Windows, was adopted for creating viruses, Trojans and worms. This last type of malware gained unusual strength, taking over almost all other types of viruses. Even though the characteristics of worms have changed over time, they all have the same objective: to spread to as many computers as possible, as quickly as possible.
With time, Visual Basic became extremely popular and Microsoft implemented part of the functionality of this language as an interpreter capable of running script files with a similar syntax.
At the same time as the Win32 platform was implemented, the first script viruses also appeared: malware inside a simple text file. These demonstrated that not only executable files (.EXE and .COM files) could carry viruses. As already seen with BAT viruses, there are also other means of propagation, proving the saying “anything that can be executed directly or through a interpreter can contain malware.” To be specific, the first viruses that infected the macros included in Microsoft Office emerged. As a result, Word, Excel, Access and PowerPoint become ways of spreading ‘lethal weapons’, which destroyed information when the user simply opened a document.
Melissa and self-executing worms
The powerful script interpreters in Microsoft Office allowed virus authors to arm their creations with the characteristics of worms. A clear example is Melissa, a Word macro virus with the characteristics of a worm that infects Word 97 and 2000 documents. This worm automatically sends itself out as an attachment to an e-mail message to the first 50 contacts in the Outlook address book on the affected computer. This technique, which has unfortunately become very popular nowadays, was first used in this virus which, in 1999, caused one of the largest epidemics in computer history in just a few days. In fact, companies like Microsoft, Intel or Lucent Technologies had to block their connections to the Internet due to the actions of Melissa.
The technique started by Melissa was developed in 1999 by viruses like VBS/Freelink, which unlike its predecessor sent itself out to all the contacts in the address book on the infected PC. This started a new wave of worms capable of sending themselves out to all the contacts in the Outlook address book on the infected computer. Of these, the worm that most stands out from the rest is VBS/LoveLetter, more commonly known as ‘I love You’, which emerged in May 2000 and caused an epidemic that caused damage estimated at 10,000 million euros. In order to get the user’s attention and help it to spread, this worm sent itself out in an e-mail message with the subject ‘ILOVEYOU’ and an attached file called ‘LOVE-LETTER-FOR-YOU.TXT.VBS’. When the user opened this attachment, the computer was infected.
As well as Melissa, in 1999 another type of virus emerged that also marked a milestone in virus history. In November of that year, VBS/BubbleBoy appeared, a new type of Internet worm written in VB Script. VBS/BubbleBoy was automatically run without the user needing to click on an attached file, as it exploited a vulnerability in Internet Explorer 5 to automatically run when the message was opened or viewed. This worm was followed in 2000 by JS/Kak.Worm, which spread by hiding behind Java Script in the auto-signature in Microsoft Outlook Express, allowing it to infect computers without the user needing to run an attached file. These were the first samples of a series of worms, which were joined later on by worms capable of attacking computers when the user is browsing the Internet.
A Basic Guide to the Internet
The Internet is a computer network made up of thousands of networks worldwide. No one knows exactly how many computers are connected to the Internet. It is certain, however, that these number in the millions.
No one is in charge of the Internet. There are organizations which develop technical aspects of this network and set standards for creating applications on it, but no governing body is in control. The Internet backbone, through which Internet traffic flows, is owned by private companies.
All computers on the Internet communicate with one another using the Transmission Control Protocol/Internet Protocol suite, abbreviated to TCP/IP. Computers on the Internet use a client/server architecture. This means that the remote server machine provides files and services to the user’s local client machine. Software can be installed on a client computer to take advantage of the latest access technology.
An Internet user has access to a wide variety of services: electronic mail, file transfer, vast information resources, interest group membership, interactive collaboration, multimedia displays, real-time broadcasting, shopping opportunities, breaking news, and much more.
The Internet consists primarily of a variety of access protocols. Many of these protocols feature programs that allow users to search for and retrieve material made available by the protocol.
——————————————————————————–
COMPONENTS OF THE INTERNET
——————————————————————————–
WORLD WIDE WEB:
The World Wide Web (abbreviated as the Web or WWW) is a system of Internet servers that supports hypertext to access several Internet protocols on a single interface. Almost every protocol type available on the Internet is accessible on the Web. This includes e-mail, FTP, Telnet, and Usenet News. In addition to these, the World Wide Web has its own protocol: Hyper Text Transfer Protocol, or HTTP. These protocols will be explained later in this document.
The World Wide Web provides a single interface for accessing all these protocols. This creates a convenient and user-friendly environment. It is no longer necessary to be conversant in these protocols within separate, command-level environments. The Web gathers together these protocols into a single system. Because of this feature, and because of the Web’s ability to work with multimedia and advanced programming languages, the Web is the fastest-growing component of the Internet.
The operation of the Web relies primarily on hypertext as its means of information retrieval. Hyper Text is a document containing words that connect to other documents. These words are called links and are selectable by the user. A single hypertext document can contain links to many documents. In the context of the Web, words or graphics may serve as links to other documents, images, video, and sound. Links may or may not follow a logical path, as each connection is programmed by the creator of the source document. Overall, the Web contains a complex virtual web of connections among a vast number of documents, graphics, videos, and sounds.
Producing hypertext for the Web is accomplished by creating documents with a language called Hyper Text Markup Language, or HTML. With HTML, tags are placed within the text to accomplish document formatting, visual features such as font size, italics and bold, and the creation of hypertext links. Graphics and multimedia may also be incorporated into an HTML document. HTML is an evolving language, with new tags being added as each upgrade of the language is developed and released. The World Wide Web Consortium (W3C), led by Web founder Tim Berners-Lee, coordinates the efforts of standardizing HTML. The W3C now calls the language XHTML and considers it to be an application of the XML language standard.
The World Wide Web consists of files, called pages or home pages, containing links to documents and resources throughout the Internet.
The Web provides a vast array of experiences including multimedia presentations, real-time collaboration, interactive pages, radio and television broadcasts, and the automatic “push” of information to a client computer. Programming languages such as Java, JavaScript, Visual Basic, Cold Fusion and XML are extending the capabilities of the Web. A growing amount of information on the Web is served dynamically from content stored in databases. The Web is therefore not a fixed entity, but one that is in a constant state of development and flux.
For more complete information about the World Wide Web, see Understanding The World Wide Web.
E-MAIL:
Electronic mail, or e-mail, allows computer users locally and worldwide to exchange messages. Each user of e-mail has a mailbox address to which messages are sent. Messages sent through e-mail can arrive within a matter of seconds.
A powerful aspect of e-mail is the option to send electronic files to a person’s e-mail address. Non-ASCII files, known as binary files, may be attached to e-mail messages. These files are referred to as MIME attachments.MIME stands for Multimedia Internet Mail Extension, and was developed to help e-mail software handle a variety of file types. For example, a document created in Microsoft Word can be attached to an e-mail message and retrieved by the recipient with the appropriate e-mail program. Many e-mail programs, including Eudora, Netscape Messenger, and Microsoft Outlook, offer the ability to read files written in HTML, which is itself a MIME type.
TELNET:
Telnet is a program that allows you to log into computers on the Internet and use online databases, library catalogs, chat services, and more. There are no graphics in Telnet sessions, just text. To Telnet to a computer, you must know its address. This can consist of words (locis.loc.gov) or numbers (140.147.254.3). Some services require you to connect to a specific port on the remote computer. In this case, type the port number after the Internet address. Example: telnet nri.reston.va.us 185.
Telnet is available on the World Wide Web. Probably the most common Web-based resources available through Telnet have been library catalogs, though most catalogs have since migrated to the Web. A link to a Telnet resource may look like any other link, but it will launch a Telnet session to make the connection. A Telnet program must be installed on your local computer and configured to your Web browser in order to work.
With the increasing popularity of the Web, Telnet has become less frequently used as a means of access to information on the Internet.
FTP:
FTP stands for File Transfer Protocol. This is both a program and the method used to transfer files between computers. Anonymous FTP is an option that allows users to transfer files from thousands of host computers on the Internet to their personal computer account. FTP sites contain books, articles, software, games, images, sounds, multimedia, course work, data sets, and more.
If your computer is directly connected to the Internet via an Ethernet cable, you can use one of several PC software programs, such as WS_FTP for Windows, to conduct a file transfer.
FTP transfers can be performed on the World Wide Web without the need for special software. In this case, the Web browser will suffice. Whenever you download software from a Web site to your local machine, you are using FTP. You can also retrieve FTP files via search engines such as FtpFind, located at hxxp://www.ftpfind.com/. This option is easiest because you do not need to know FTP program commands.
E-MAIL DISCUSSION GROUPS:
One of the benefits of the Internet is the opportunity it offers to people worldwide to communicate via e-mail. The Internet is home to a large community of individuals who carry out active discussions organized around topic-oriented forums distributed by e-mail. These are administered by software programs. Probably the most common program is the listserv.
A great variety of topics are covered by listservs, many of them academic in nature. When you subscribe to a listserv, messages from other subscribers are automatically sent to your electronic mailbox. You subscribe to a listserv by sending an e-mail message to a computer program called a listserver. Listservers are located on computer networks throughout the world. This program handles subscription information and distributes messages to and from subscribers. You must have a e-mail account to participate in a listserv discussion group. Visit Tile.net at hxxp://tile.net/ to see an example of a site that offers a searchable collection of e-mail discussion groups.
Majordomo and Listproc are two other programs that administer e-mail discussion groups. The commands for subscribing to and managing your list memberships are similar to those of listserv.
USENET NEWS:
Usenet News is a global electronic bulletin board system in which millions of computer users exchange information on a vast range of topics. The major difference between Usenet News and e-mail discussion groups is the fact that Usenet messages are stored on central computers, and users must connect to these computers to read or download the messages posted to these groups. This is distinct from e-mail distribution, in which messages arrive in the electronic mailboxes of each list member.
Usenet itself is a set of machines that exchanges messages, or articles, from Usenet discussion forums, called newsgroups. Usenet administrators control their own sites, and decide which (if any) newsgroups to sponsor and which remote newsgroups to allow into the system.
There are thousands of Usenet newsgroups in existence. While many are academic in nature, numerous newsgroups are organized around recreational topics. Much serious computer-related work takes place in Usenet discussions. A small number of e-mail discussion groups also exist as Usenet newsgroups.
The Usenet news feed can be read by a variety of newsreader software programs. For example, the Netscape suite comes with a newsreader program called Messenger. Newsreaders are also available as standalone products.
FAQ, RFC, FYI:
FAQ stands for Frequently Asked Questions. These are periodic postings to Usenet newsgroups that contain a wealth of information related to the topic of the newsgroup. Many FAQs are quite extensive. FAQs are available by subscribing to individual Usenet newsgroups. A Web-based collection of FAQ resources has been collected by The Internet FAQ Consortium and is available at hxxp://www.faqs.org/.
RFC stands for Request for Comments. These are documents created by and distributed to the Internet community to help define the nuts and bolts of the Internet. They contain both technical specifications and general information.
FYI stands for For Your Information. These notes are a subset of RFCs and contain information of interest to new Internet users.
Links to indexes of all three of these information resources are available on the University Libraries Web site at hxxp://library.albany.edu/reference/faqs.html.
CHAT & INSTANT MESSENGING:
Chat programs allow users on the Internet to communicate with each other by typing in real time. They are sometimes included as a feature of a Web site, where users can log into the “chat room” to exchange comments and information about the topics addressed on the site. Chat may take other, more wide-ranging forms. For example, America Online is well known for sponsoring a number of topical chat rooms.
Internet Relay Chat (IRC) is a service through which participants can communicate to each other on hundreds of channels. These channels are usually based on specific topics. While many topics are frivolous, substantive conversations are also taking place. To access IRC, you must use an IRC software program.
A variation of chat is the phenomenon of instant messenging. With instant messenging, a user on the Web can contact another user currently logged in and type a conversation. Most famous is America Online’s Instant Messenger. ICQ, MSN and Yahoo are other commonly-used chat programs.
Other types of real-time communication are addressed in the tutorial Understanding the World Wide Web.
If you wanna remove those nasty ads from the pages which waste lot of time and bandwidth then here is something for you I believe it will help you a lot.
How it works:
It’s possible to set up a name server as authoritative for any domain you choose, allowing you to specify the DNS records for that domain. You can also configure most computers to be sort of mini-nameservers for themselves, so that they check their own DNS records before asking a nameserver. Either way, you get to say what hostname points to what IP address. If you haven’t guessed already, the way you block ads it to provide bogus information about the domains we don’t want to see – ie, all those servers out there that dedicate their existence to spewing out banner ads.
The hosts file
Probably the most common way people block ads like this is with something called the “hosts file”. The hosts file is a simple list of hostnames and their corresponding IP addresses, which your computer looks at every time you try and contact a previously unknown hostname. If it finds an entry for the computer you’re trying to reach, it sets the IP address for that computer to be what ever’s in the hosts file.
127.0.0.1 is a special IP address which, to a computer, always means that computer. Any time a machine sends a network request to 127.0.0.1, it is talking to itself. This is very useful when it comes to blocking ads, because all we have to do is specify the IP address of any ad server to be 127.0.0.1. And to do that, all we have to do is edit the hosts file. What will happen then is something like this:
1. you visit a web page
2. the web page contains a banner ad stored on the server “ads.example.com”
3. your computer says “ads.example.com? never heard of it. wait a second, let’s see if I’ve got the number on me…”
4. your computer finds its hosts file and checks to see if ads.example.com is listed
5. it finds the hostname, which points to 127.0.0.1
6. “great”, says the computer, and sends off a request to 127.0.0.1 for the banner ad that’s supposed to be on the page
7. “oh”, says the computer, and fails to show anything because it just sent a request to itself for a banner ad
Where’s my hosts file?
* Windows 95 / 98 / ME: C:\Windows (I think)
* Windows NT: C:\WinNT\hosts
* Windows 2000: C:\WinNT\system32\drivers\etc\
* Windows XP: C:\Windows\System32\drivers\etc
* FreeBSD / Linux / Mac OS X / Unix operating systems: /etc/hosts
The format of the hosts file is very simple – IP address, whitespace, then a list of hostnames (except for older Macs; please see above). However, you don’t need to know anything about the format if you don’t want to as you can just view the list hosts file.
Of course, that’s not the only way to use the list, but it’s probably the most simple for most people.
A simple tool to find music on the net
Exploseek is a nice simple tool to find music on the net. It is possible to use the major search engines to type your queries, but if you use this tool it will be much easier as some of you have probably seen already. We always try to improve the queries, if possible, and will update it at random times. Further you don’t need to install a peer-to-peer program with possible spyware and other security issues, the price to pay is that you will not always find as much as such a program, but on a lucky day you find a load of music.
Useful information on Internet Merchant Account
Choosing An Internet Merchant Account:
Surf to Google and perform a search on “Internet Merchant Account”. The results are staggering (2,300,000 results!) If you have created a web based business and need to accept credit card payments, your choices are limitless. Before you partner with a provider, take time to understand the different components of Internet credit card processing, and know what to look for in a merchant provider.
How It Works:
Accepting credit card payments through your web site actually requires multiple components. Between a paying customer and your bank account, three layers exist:
Payment Gateway – This is the code that will transmit a customer’s order to and from an Internet merchant account provider. The payment gateway provides you the ability to accept customer billing information (credit card number, credit card type, expiration date, and payment amount) and the necessary validation steps that must be followed before the credit card is actually billed.
Internet Merchant Account – A Merchant Account is an account with a financial institution or bank, which enables you to accept credit card payments from your clients. The payment gateway actually transmits the billing information to the Internet merchant account provider. Unfortunately, most local banks do not provide Internet merchant account capability.
The main reason why most local financial institutions or banks do not want to provide online merchant accounts is because transactions conducted over the Internet are totally different from face to face transactions where a signature is required to authorize the purchase. This makes online transactions prone to credit card fraud. Fraud protection should be one of your primary considerations when choosing an Internet merchant account provider.
Web Site – Regardless of which merchant provider and gateway service you choose, your web site will need to integrate with your service providers. Most providers include detailed web integration instructions.
How Much Does It Cost ?
Understanding the total costs of your merchant provider can be tricky. Remember my Google example – there are more merchant account providers than there are people looking for internet merchant accounts so ask questions and be picky! Typically, an internet merchant account will have three types of costs:
– Up Front Application Fees
– On Going Fixed Fee
– Discount Rate
– Fixed Transaction Fee
– Termination Fees
– Miscellaneous Fees
Let us discuss each type of cost:
* Up Front Application Fees
Many Internet merchant accounts will require an up front application fee. This fee, supposedly, is to cover their costs for processing your application. In case you choose not to open an Internet merchant account, they still cover their initial costs. Although common, many providers waive these fees and I recommend that you choose a provider that does not require an up front fee.
* On Going Fixed Fee
Most all Internet merchant providers require a monthly fixed fee or “statement fee” as it is commonly named, which is simply another way to cover their costs and make money. You will be hard pressed to find a provider that does not require this type of fee on a monthly basis. However, do not choose an Internet merchant account that requires more than $10 per month. Additionally, most Internet merchant providers require a monthly minimum (usually $25). The bottom line is that you will be paying at least $25 per month (on top of the monthly statement fee) for your account.
* Discount Rate
Usually, the discount rate will be between 2 and 4 percent. The discount rate is the sales commission the provider earns on each sale. For example, if the discount rate offered is 3%, and you receive a sale over your web site for $20, you will owe 60 cents to your Internet merchant provider.
* Fixed Transaction Fee
Usually between $0.20 and $0.30, the fixed transaction fee is the fixed fee portion of each sale. Unlike the discount rate, the fixed transaction fee is the same for every transaction. Whether you get a $1 sale or a $100 sale, the transaction fee will be the same.
* Termination Fee
A bit more hidden in the small print, a termination fee can apply if you cancel your merchant account within a specified period of time (usually within one year). But beware, some merchant providers require a three year commitment!
* Miscellaneous Fees
If a customer requests a refund and they want their credit card credited, an Internet merchant provider will charge you a separate fee (usually between $10 – $20). Read the contract carefully, as other special fees may apply.
Putting It All Together
Now that the different fees have been explained, let us look at an example set of transactions to help understand what an Internet merchant account may cost your business on a monthly basis.
I have created a simple formula to help you calculate your monthly charges:
Total Charges = Statement Fee + Number of Transactions x (Average Sale x Discount Rate + Fixed Transaction Fee) + (Number of Charge backs x Charge back Fee)
For example, let us see you sell widgets over the Internet. The sales price for each widget is $10. You typically have 100 sales per month and about 5 people request refunds (charge backs). For this example, let us assume you have signed up with Jones&Jones Internet merchant account services and have the following terms:
Discount Rate – %2.5
Statement Fee – $10
Fixed Transaction Fee – $0.30
Charge back Fee – $15
Using my formula above, your monthly Jones&Jones charges will be:
Total Charges = 10 + 100 x (10 x .025 + 0.3) + (5 x 15) = $140
You can calculate your monthly sales revenue by multiplying your sales volume by your price:
Monthly Sales Revenue = 100 x $10 = $1000
Your Internet merchant provider is costing you 14% of your total sales.
Making Your Decision
Before you choose and Internet merchant provider, understand all of the cost components. Use your current or projected sales data to forecast what your Internet merchant account costs will be. Planning ahead can save you time and money.
I hope this insight will provide a good use for those who want to do business on the web.
Evolution Of Computer Viruses History Of Viruses
part 1:
Like any other field in computer science, viruses have evolved -a great deal indeed- over the years. In the series of press releases which start today, we will look at the origins and evolution of malicious code since it first appeared up to the present.
Going back to the origin of viruses, it was in 1949 that Mathematician John Von Neumann described self-replicating programs which could resemble computer viruses as they are known today. However, it was not until the 60s that we find the predecessor of current viruses. In that decade, a group of programmers developed a game called Core Wars, which could reproduce every time it was run, and even saturate the memory of other players’ computers. The creators of this peculiar game also created the first antivirus, an application named Reeper, which could destroy copies created by Core Wars.
However, it was only in 1983 that one of these programmers announced the existence of Core Wars, which was described the following year in a prestigious scientific magazine: this was actually the starting point of what we call computer viruses today.
At that time, a still young MS-DOS was starting to become the preeminent operating system worldwide. This was a system with great prospects, but still many deficiencies as well, which arose from software developments and the lack of many hardware elements known today. Even like this, this new operating system became the target of a virus in 1986: Brain, a malicious code created in Pakistan which infected boot sectors of disks so that their contents could not be accessed. That year also saw the birth of the first Trojan: an application called PC-Write.
Shortly after, virus writers realized that infecting files could be even more harmful to systems. In 1987, a virus called Suriv-02 appeared, which infected COM files and opened the door to the infamous viruses Jerusalem or Viernes 13. However, the worst was still to come: 1988 set the date when the “Morris worm” appeared, infecting 6,000 computers.
From that date up to 1995 the types of malicious codes that are known today started being developed: the first macro viruses appeared, polymorphic viruses … Some of these even triggered epidemics, such as MichaelAngelo. However, there was an event that changed the virus scenario worldwide: the massive use of the Internet and e-mail. Little by little, viruses started adapting to this new situation until the appearance, in 1999, of Melissa, the first malicious code to cause a worldwide epidemic, opening a new era for computer viruses.
part 2:
This second installment of ‘The evolution of viruses’ will look at how malicious code used to spread before use of the Internet and e-mail became as commonplace as it is today, and the main objectives of the creators of those earlier viruses.
Until the worldwide web and e-mail were adopted as a standard means of communication the world over, the main mediums through which viruses spread were floppy disks, removable drives, CDs, etc., containing files that were already infected or with the virus code in an executable boot sector.
When a virus entered a system it could go memory resident, infecting other files as they were opened, or it could start to reproduce immediately, also infecting other files on the system. The virus code could also be triggered by a certain event, for example when the system clock reached a certain date or time. In this case, the virus creator would calculate the time necessary for the virus to spread and then set a date –often with some particular significance- for the virus to activate. In this way, the virus would have an incubation period during which it didn’t visibly affect computers, but just spread from one system to another waiting for ‘D-day’ to launch its payload. This incubation period would be vital to the virus successfully infecting as many computers as possible.
One classic example of a destructive virus that lay low before releasing its payload was CIH, also known as Chernobyl. The most damaging version of this malicious code activated on April 26, when it would try to overwrite the flash-BIOS, the memory which includes the code needed to control PC devices. This virus, which first appeared in June 1998, had a serious impact for over two years and still continues to infect computers today.
Because of the way in which they propagate, these viruses spread very slowly, especially in comparison to the speed of today’s malicious code. Towards the end of the Eighties, for example, the Friday 13th (or Jerusalem) virus needed a long time to actually spread and continued to infect computers for some years. In contrast, experts reckon that in January 2003, SQLSlammer took just ten minutes to cause global communication problems across the Internet.
Notoriety versus stealth
For the most part, in the past, the activation of a malicious code triggered a series of on screen messages or images, or caused sounds to be emitted to catch the user’s attention. Such was the case with the Ping Pong virus, which displayed a ball bouncing from one side of the screen to another. This kind of elaborate display was used by the creator of the virus to gain as much notoriety as possible. Nowadays however, the opposite is the norm, with virus authors trying to make malicious code as discreet as possible, infecting users’ systems without them noticing that anything is amiss.
part 3:
This third installment of ‘The evolution of viruses’ will look at how the Internet and e-mail changed the propagation techniques used by computer viruses.
Internet and e-mail revolutionized communications. However, as expected, virus creators didn’t take long to realize that along with this new means of communication, an excellent way of spreading their creations far and wide had also dawned. Therefore, they quickly changed their aim from infecting a few computers while drawing as much attention to themselves as possible, to damaging as many computers as possible, as quickly as possible. This change in strategy resulted in the first global virus epidemic, which was caused by the Melissa worm.
With the appearance of Melissa, the economic impact of a virus started to become an issue. As a result, users -above all companies- started to become seriously concerned about the consequences of viruses on the security of their computers. This is how users discovered antivirus programs, which started to be installed widely. However, this also brought about a new challenge for virus writers, how to slip past this protection and how to persuade users to run infected files.
The answer to which of these virus strategies was the most effective came in the form of a new worm: Love Letter, which used a simple but effective ruse that could be considered an early type of social engineering. This strategy involves inserting false messages that trick users into thinking that the message includes anything, except a virus. This worm’s bait was simple; it led users to believe that they had received a love letter.
This technique is still the most widely used. However, it is closely followed by another tactic that has been the center of attention lately: exploiting vulnerabilities in commonly used software. This strategy offers a range of possibilities depending on the security hole exploited. The first malicious code to use this method –and quite successfully- were the BubbleBoy and Kakworm worms. These worms exploited a vulnerability in Internet Explorer by inserting HTML code in the body of the e-mail message, which allowed them to run automatically, without needing the user to do a thing.
Vulnerabilities allow many different types of actions to be carried out. For example, they allow viruses to be dropped on computers directly from the Internet -such as the Blaster worm-. In fact, the effects of the virus depend on the vulnerability that the virus author tries to exploit.
part 4:
In the early days of computers, there were relatively few PCs likely to contain “sensitive” information, such as credit card numbers or other financial data, and these were generally limited to large companies that had already incorporated computers into working processes.
In any event, information stored in computers was not likely to be compromised, unless the computer was connected to a network through which the information could be transmitted. Of course, there were exceptions to this and there were cases in which hackers perpetrated frauds using data stored in IT systems. However, this was achieved through typical hacking activities, with no viruses involved.
The advent of the Internet however caused virus creators to change their objectives, and, from that moment on, they tried to infect as many computers as possible in the shortest time. Also, the introduction of Internet services -like e-banking or online shopping- brought in another change. Some virus creators started writing malicious codes not to infect computers, but, to steal confidential data associated to those services. Evidently, to achieve this, they needed viruses that could infect many computers silently.
Their malicious labor was finally rewarded with the appearance, in 1986, of a new breed of malicious code generically called “Trojan Horse”, or simply “Trojan”. This first Trojan was called PC-Write and tried to pass itself off as the shareware version of a text processor. When run, the Trojan displayed a functional text processor on screen. The problem was that, while the user wrote, PC-Write deleted and corrupted files on the computers’ hard disk.
After PC-Write, this type of malicious code evolved very quickly to reach the stage of present-day Trojans. Today, many of the people who design Trojans to steal data cannot be considered virus writers but simply thieves who, instead of using blowtorches or dynamite have turned to viruses to commit their crimes. Ldpinch.W or the Bancos or Tolger families of Trojans are examples of this
part 5:
Even though none of them can be left aside, some particular fields of computer science have played a more determinant role than others with regard to the evolution of viruses. One of the most influential fields has been the development of programming languages.
These languages are basically a means of communication with computers in order to tell them what to do. Even though each of them has its own specific development and formulation rules, computers in fact understand only one language called “machine code”.
Programming languages act as an interpreter between the programmer and the computer. Obviously, the more directly you can communicate with the computer, the better it will understand you, and more complex actions you can ask it to perform.
According to this, programming languages can be divided into “low and high level” languages, depending on whether their syntax is more understandable for programmers or for computers. A “high level” language uses expressions that are easily understandable for most programmers, but not so much for computers. Visual Basic and C are good examples of this type of language.
On the contrary, expressions used by “low level” languages are closer to machine code, but are very difficult to understand for someone who has not been involved in the programming process. One of the most powerful, most widely used examples of this type of language is “assembler”.
In order to explain the use of programming languages through virus history, it is necessary to refer to hardware evolution. It is not difficult to understand that an old 8-bit processor does not have the power of modern 64-bit processors, and this of course, has had an impact on the programming languages used.
In this and the next installments of this series, we will look at the different programming languages used by virus creators through computer history:
– Virus antecessors: Core Wars
As was already explained in the first chapter of this series, a group of programs called Core Wars, developed by engineers at an important telecommunications company, are considered the antecessors of current-day viruses. Computer science was still in the early stages and programming languages had hardly developed. For this reason, authors of these proto-viruses used a language that was almost equal to machine code to program them.
Curiously enough, it seems that one of the Core Wars programmers was Robert Thomas Morris, whose son programmed -years later- the “Morris worm”. This malicious code became extraordinarily famous since it managed to infect 6,000 computers, an impressive figure for 1988.
– The new gurus of the 8-bits and the assembler language.
The names Altair, IMSAI and Apple in USA and Sinclair, Atari and Commodore in Europe, bring memories of times gone by, when a new generation of computer enthusiasts “fought” to establish their place in the programming world. To be the best, programmers needed to have profound knowledge of machine code and assembler, as interpreters of high-level languages used too much run time. BASIC, for example, was a relatively easy to learn language which allowed users to develop programs simply and quickly. It had however, many limitations.
This caused the appearance of two groups of programmers: those who used assembler and those who turned to high-level languages (BASIC and PASCAL, mainly).
Computer aficionados of the time enjoyed themselves more by programming useful software than malware. However, 1981 saw the birth of what can be considered the first 8-bit virus. Its name was “Elk Cloner”, and was programmed in machine code. This virus could infect Apple II systems and displayed a message when it infected a computer.
part 6:
Computer viruses evolve in much the same way as in other areas of IT. Two of the most important factors in understanding how viruses have reached their current level are the development of programming languages and the appearance of increasingly powerful hardware.
In 1981, almost at the same time as Elk Kloner (the first virus for 8-bit processors) made its appearance, a new operating system was growing in popularity. Its full name was Microsoft Disk Operating System, although computer buffs throughout the world would soon refer to it simply as DOS.
DOS viruses
The development of MS DOS systems occurred in parallel to the appearance of new, more powerful hardware. Personal computers were gradually establishing themselves as tools that people could use in their everyday lives, and the result was that the number of PCs users grew substantially. Perhaps inevitably, more users also started creating viruses. Gradually, we witnessed the appearance of the first viruses and Trojans for DOS, written in assembler language and demonstrating a degree of skill on the part of their authors.
Far less programmers know assembler language than are familiar with high-level languages that are far easier to learn. Malicious code written in Fortran, Basic, Cobol, C or Pascal soon began to appear. The last two languages, which are well established and very powerful, are the most widely used, particularly in their TurboC and Turbo Pascal versions. This ultimately led to the appearance of “virus families”: that is, viruses that are followed by a vast number of related viruses which are slightly modified forms of the original code.
Other users took the less ‘artistic’ approach of creating destructive viruses that did not require any great knowledge of programming. As a result, batch processing file viruses or BAT viruses began to appear.
Win16 viruses
The development of 16-bit processors led to a new era in computing. The first consequence was the birth of Windows, which, at the time, was just an application to make it easier to handle DOS using a graphic interface.
The structure of Windows 3.xx files is rather difficult to understand, and the assembler language code is very complicated, as a result of which few programmers initially attempted to develop viruses for this platform. But this problem was soon solved thanks to the development of programming tools for high-level languages, above all Visual Basic. This application is so effective that many virus creators adopted it as their ‘daily working tool’. This meant that writing a virus had become a very straightforward task, and viruses soon appeared in their hundreds. This development was accompanied by the appearance of the first Trojans able to steal passwords. As a result, more than 500 variants of the AOL Trojan family -designed to steal personal information from infected computers- were identified.
part 7:
This seventh edition on the history of computer viruses will look at how the development of Windows and Visual Basic has influenced the evolution of viruses, as with the development of these, worldwide epidemics also evolved such as the first one caused by Melissa in 1999.
While Windows changed from being an application designed to make DOS easier to manage to a 32-bit platform and operating system in its own right, virus creators went back to using assembler as the main language for programming viruses.
Versions 5 and 6 of Visual Basic (VB) were developed, making it the preferred tool, along with Borland Delphi (the Pascal development for the Windows environment), for Trojan and worm writers. Then, Visual C, a powerful environment developed in C for Windows, was adopted for creating viruses, Trojans and worms. This last type of malware gained unusual strength, taking over almost all other types of viruses. Even though the characteristics of worms have changed over time, they all have the same objective: to spread to as many computers as possible, as quickly as possible.
With time, Visual Basic became extremely popular and Microsoft implemented part of the functionality of this language as an interpreter capable of running script files with a similar syntax.
At the same time as the Win32 platform was implemented, the first script viruses also appeared: malware inside a simple text file. These demonstrated that not only executable files (.EXE and .COM files) could carry viruses. As already seen with BAT viruses, there are also other means of propagation, proving the saying “anything that can be executed directly or through a interpreter can contain malware.” To be specific, the first viruses that infected the macros included in Microsoft Office emerged. As a result, Word, Excel, Access and PowerPoint become ways of spreading ‘lethal weapons’, which destroyed information when the user simply opened a document.
Melissa and self-executing worms
The powerful script interpreters in Microsoft Office allowed virus authors to arm their creations with the characteristics of worms. A clear example is Melissa, a Word macro virus with the characteristics of a worm that infects Word 97 and 2000 documents. This worm automatically sends itself out as an attachment to an e-mail message to the first 50 contacts in the Outlook address book on the affected computer. This technique, which has unfortunately become very popular nowadays, was first used in this virus which, in 1999, caused one of the largest epidemics in computer history in just a few days. In fact, companies like Microsoft, Intel or Lucent Technologies had to block their connections to the Internet due to the actions of Melissa.
The technique started by Melissa was developed in 1999 by viruses like VBS/Freelink, which unlike its predecessor sent itself out to all the contacts in the address book on the infected PC. This started a new wave of worms capable of sending themselves out to all the contacts in the Outlook address book on the infected computer. Of these, the worm that most stands out from the rest is VBS/LoveLetter, more commonly known as ‘I love You’, which emerged in May 2000 and caused an epidemic that caused damage estimated at 10,000 million euros. In order to get the user’s attention and help it to spread, this worm sent itself out in an e-mail message with the subject ‘ILOVEYOU’ and an attached file called ‘LOVE-LETTER-FOR-YOU.TXT.VBS’. When the user opened this attachment, the computer was infected.
As well as Melissa, in 1999 another type of virus emerged that also marked a milestone in virus history. In November of that year, VBS/BubbleBoy appeared, a new type of Internet worm written in VB Script. VBS/BubbleBoy was automatically run without the user needing to click on an attached file, as it exploited a vulnerability in Internet Explorer 5 to automatically run when the message was opened or viewed. This worm was followed in 2000 by JS/Kak.Worm, which spread by hiding behind Java Script in the auto-signature in Microsoft Outlook Express, allowing it to infect computers without the user needing to run an attached file. These were the first samples of a series of worms, which were joined later on by worms capable of attacking computers when the user is browsing the Internet.
Use Gmail With Msn Messenger
i think all of you know it but if someone dont than here it is
go to this page:
https://register.passport.net/default.srf?sl=1
enter you gmail account as the email address
fill all the other blanks and continue the registration
go to your gmail account and verify the registration and know sign in with msn
actually this works will all emails not only gmail
A Basic Guide to the Internet
The Internet is a computer network made up of thousands of networks worldwide. No one knows exactly how many computers are connected to the Internet. It is certain, however, that these number in the millions.
No one is in charge of the Internet. There are organizations which develop technical aspects of this network and set standards for creating applications on it, but no governing body is in control. The Internet backbone, through which Internet traffic flows, is owned by private companies.
All computers on the Internet communicate with one another using the Transmission Control Protocol/Internet Protocol suite, abbreviated to TCP/IP. Computers on the Internet use a client/server architecture. This means that the remote server machine provides files and services to the user’s local client machine. Software can be installed on a client computer to take advantage of the latest access technology.
An Internet user has access to a wide variety of services: electronic mail, file transfer, vast information resources, interest group membership, interactive collaboration, multimedia displays, real-time broadcasting, shopping opportunities, breaking news, and much more.
The Internet consists primarily of a variety of access protocols. Many of these protocols feature programs that allow users to search for and retrieve material made available by the protocol.
——————————————————————————–
COMPONENTS OF THE INTERNET
——————————————————————————–
WORLD WIDE WEB:
The World Wide Web (abbreviated as the Web or WWW) is a system of Internet servers that supports hypertext to access several Internet protocols on a single interface. Almost every protocol type available on the Internet is accessible on the Web. This includes e-mail, FTP, Telnet, and Usenet News. In addition to these, the World Wide Web has its own protocol: Hyper Text Transfer Protocol, or HTTP. These protocols will be explained later in this document.
The World Wide Web provides a single interface for accessing all these protocols. This creates a convenient and user-friendly environment. It is no longer necessary to be conversant in these protocols within separate, command-level environments. The Web gathers together these protocols into a single system. Because of this feature, and because of the Web’s ability to work with multimedia and advanced programming languages, the Web is the fastest-growing component of the Internet.
The operation of the Web relies primarily on hypertext as its means of information retrieval. Hyper Text is a document containing words that connect to other documents. These words are called links and are selectable by the user. A single hypertext document can contain links to many documents. In the context of the Web, words or graphics may serve as links to other documents, images, video, and sound. Links may or may not follow a logical path, as each connection is programmed by the creator of the source document. Overall, the Web contains a complex virtual web of connections among a vast number of documents, graphics, videos, and sounds.
Producing hypertext for the Web is accomplished by creating documents with a language called Hyper Text Markup Language, or HTML. With HTML, tags are placed within the text to accomplish document formatting, visual features such as font size, italics and bold, and the creation of hypertext links. Graphics and multimedia may also be incorporated into an HTML document. HTML is an evolving language, with new tags being added as each upgrade of the language is developed and released. The World Wide Web Consortium (W3C), led by Web founder Tim Berners-Lee, coordinates the efforts of standardizing HTML. The W3C now calls the language XHTML and considers it to be an application of the XML language standard.
The World Wide Web consists of files, called pages or home pages, containing links to documents and resources throughout the Internet.
The Web provides a vast array of experiences including multimedia presentations, real-time collaboration, interactive pages, radio and television broadcasts, and the automatic “push” of information to a client computer. Programming languages such as Java, JavaScript, Visual Basic, Cold Fusion and XML are extending the capabilities of the Web. A growing amount of information on the Web is served dynamically from content stored in databases. The Web is therefore not a fixed entity, but one that is in a constant state of development and flux.
For more complete information about the World Wide Web, see Understanding The World Wide Web.
E-MAIL:
Electronic mail, or e-mail, allows computer users locally and worldwide to exchange messages. Each user of e-mail has a mailbox address to which messages are sent. Messages sent through e-mail can arrive within a matter of seconds.
A powerful aspect of e-mail is the option to send electronic files to a person’s e-mail address. Non-ASCII files, known as binary files, may be attached to e-mail messages. These files are referred to as MIME attachments.MIME stands for Multimedia Internet Mail Extension, and was developed to help e-mail software handle a variety of file types. For example, a document created in Microsoft Word can be attached to an e-mail message and retrieved by the recipient with the appropriate e-mail program. Many e-mail programs, including Eudora, Netscape Messenger, and Microsoft Outlook, offer the ability to read files written in HTML, which is itself a MIME type.
TELNET:
Telnet is a program that allows you to log into computers on the Internet and use online databases, library catalogs, chat services, and more. There are no graphics in Telnet sessions, just text. To Telnet to a computer, you must know its address. This can consist of words (locis.loc.gov) or numbers (140.147.254.3). Some services require you to connect to a specific port on the remote computer. In this case, type the port number after the Internet address. Example: telnet nri.reston.va.us 185.
Telnet is available on the World Wide Web. Probably the most common Web-based resources available through Telnet have been library catalogs, though most catalogs have since migrated to the Web. A link to a Telnet resource may look like any other link, but it will launch a Telnet session to make the connection. A Telnet program must be installed on your local computer and configured to your Web browser in order to work.
With the increasing popularity of the Web, Telnet has become less frequently used as a means of access to information on the Internet.
FTP:
FTP stands for File Transfer Protocol. This is both a program and the method used to transfer files between computers. Anonymous FTP is an option that allows users to transfer files from thousands of host computers on the Internet to their personal computer account. FTP sites contain books, articles, software, games, images, sounds, multimedia, course work, data sets, and more.
If your computer is directly connected to the Internet via an Ethernet cable, you can use one of several PC software programs, such as WS_FTP for Windows, to conduct a file transfer.
FTP transfers can be performed on the World Wide Web without the need for special software. In this case, the Web browser will suffice. Whenever you download software from a Web site to your local machine, you are using FTP. You can also retrieve FTP files via search engines such as FtpFind, located at hxxp://www.ftpfind.com/. This option is easiest because you do not need to know FTP program commands.
E-MAIL DISCUSSION GROUPS:
One of the benefits of the Internet is the opportunity it offers to people worldwide to communicate via e-mail. The Internet is home to a large community of individuals who carry out active discussions organized around topic-oriented forums distributed by e-mail. These are administered by software programs. Probably the most common program is the listserv.
A great variety of topics are covered by listservs, many of them academic in nature. When you subscribe to a listserv, messages from other subscribers are automatically sent to your electronic mailbox. You subscribe to a listserv by sending an e-mail message to a computer program called a listserver. Listservers are located on computer networks throughout the world. This program handles subscription information and distributes messages to and from subscribers. You must have a e-mail account to participate in a listserv discussion group. Visit Tile.net at hxxp://tile.net/ to see an example of a site that offers a searchable collection of e-mail discussion groups.
Majordomo and Listproc are two other programs that administer e-mail discussion groups. The commands for subscribing to and managing your list memberships are similar to those of listserv.
USENET NEWS:
Usenet News is a global electronic bulletin board system in which millions of computer users exchange information on a vast range of topics. The major difference between Usenet News and e-mail discussion groups is the fact that Usenet messages are stored on central computers, and users must connect to these computers to read or download the messages posted to these groups. This is distinct from e-mail distribution, in which messages arrive in the electronic mailboxes of each list member.
Usenet itself is a set of machines that exchanges messages, or articles, from Usenet discussion forums, called newsgroups. Usenet administrators control their own sites, and decide which (if any) newsgroups to sponsor and which remote newsgroups to allow into the system.
There are thousands of Usenet newsgroups in existence. While many are academic in nature, numerous newsgroups are organized around recreational topics. Much serious computer-related work takes place in Usenet discussions. A small number of e-mail discussion groups also exist as Usenet newsgroups.
The Usenet news feed can be read by a variety of newsreader software programs. For example, the Netscape suite comes with a newsreader program called Messenger. Newsreaders are also available as standalone products.
FAQ, RFC, FYI:
FAQ stands for Frequently Asked Questions. These are periodic postings to Usenet newsgroups that contain a wealth of information related to the topic of the newsgroup. Many FAQs are quite extensive. FAQs are available by subscribing to individual Usenet newsgroups. A Web-based collection of FAQ resources has been collected by The Internet FAQ Consortium and is available at hxxp://www.faqs.org/.
RFC stands for Request for Comments. These are documents created by and distributed to the Internet community to help define the nuts and bolts of the Internet. They contain both technical specifications and general information.
FYI stands for For Your Information. These notes are a subset of RFCs and contain information of interest to new Internet users.
Links to indexes of all three of these information resources are available on the University Libraries Web site at hxxp://library.albany.edu/reference/faqs.html.
CHAT & INSTANT MESSENGING:
Chat programs allow users on the Internet to communicate with each other by typing in real time. They are sometimes included as a feature of a Web site, where users can log into the “chat room” to exchange comments and information about the topics addressed on the site. Chat may take other, more wide-ranging forms. For example, America Online is well known for sponsoring a number of topical chat rooms.
Internet Relay Chat (IRC) is a service through which participants can communicate to each other on hundreds of channels. These channels are usually based on specific topics. While many topics are frivolous, substantive conversations are also taking place. To access IRC, you must use an IRC software program.
A variation of chat is the phenomenon of instant messenging. With instant messenging, a user on the Web can contact another user currently logged in and type a conversation. Most famous is America Online’s Instant Messenger. ICQ, MSN and Yahoo are other commonly-used chat programs.
Other types of real-time communication are addressed in the tutorial Understanding the World Wide Web.
Change The Storage Location Of ‘my Documents’, a bit safer for when your PC crashes….
Normally windows saves the “my Documents” folder on your system-drive [the drive you have installed your operating system]. But when you right-click on it and go to properties, you can change the location where you want windows to save your Documents folder.
You should have a partition set up with just windows on it, and all your things you want to keep are on different partitions/disks. So now you can put My Documents on another partition than where you have windows installed. If windows screws up and you have to format your system-drive again, your documents will be spared at least…
Rohit Mahatara
♦ January 19, 2012
♦ Leave a comment
कम्प्यूटर बेसिक कोर्स
(Basic Computer Course)
कम्प्यूटर भनेको के हो ?
Computer एउटा Electronic यन्त्र हो । जसले इनपुट लिन्छ र उच्चबेगमा प्रयोगकर्ता ले दिएको निर्देशअनुसार प्राप्तडाटालाई प्रशोधन गरि कार्यसम्पादन गरेर अर्थपुर्ण नतिजा प्रस्तुत गर्ने र डाटा भण्डार गर्ने काम गर्छ । जुन हाम्रो लागि अति उपयोगी हुन्छ जसलाई कम्प्यूटर भनिन्छ ।
“A computer is an electronic device which can perform mathematical calculation and logical operation at very high speed”
COMPUTER FULL FORM
C: – Commonly (साधारण)
O: – Operating (सञ्चालन)
M: – Machine (यन्त्र)
P: – Purpose (उद्देश्य)
U: – Use Full (उपयोगी)
T: – Technology (प्रविधि)
E: – Education (शिक्षा)
R: – Research (खोज तलाश)
कम्प्युटरको परिभाषा
कम्प्युटर एक इलेक्ट्रोनिक यन्त्र हो जसले अत्यन्तै उच्च वेगमा तर्कपूर्ण तरिकाले कार्य सम्पादन गर्न अधिकांश गणितीय समस्याहरु हल गर्न डाटा भण्डार गर्न तथा नतिजा छाप्न सक्तछ । साँच्चै भन्ने हो भने कम्प्युटर विद्युत्शक्तिबाट सञ्चालित मानवनिर्मित एक यन्त्र हो । यसले एक सेकेन्डमा दसैंकरोड निर्देशनहरु पालना गर्न सक्तछ ।यसले आफ्नो आन्तरिक भण्डारमा करोडौं अक्षर वा अङ्कहरु सञ्चयगर्न सक्तछ भने बाह्य भण्डारमा (floppy, Hard disk, Cd-rom,Tape, Pen Drive, Memori Card )सयौ खर्ब अङक,अक्षरहरु,चित्रहरु, ग्राफहरु, चलचित्रहरु तथा आवाजहरु भण्डार गर्ने क्षमता राख्दछ । यी सम्पुर्ण आँकडाहरुलाई पढन, छानबिन गर्न, सूचनाको रुपमा तालिका तयार गर्न र आवश्यकताअनुसार केहि सेकेन्डभित्रै पूरा गर्न पनि सक्तछ । एउटा कम्प्यूटरले अर्को कम्प्यूटरसँग कुराकानी गर्ने र आफु व्यस्त भएको समयमा आफ्नो काम अरुलाई वितरण गर्नुका साथै अरुसँग मिलेर कार्य गर्न समेत सक्तछ ।हजारौ किलोमिटर टाढा रहेको कम्प्यूटरसँग आकाशमा स्थापित सेटलाईटको माध्यमबाट कुराकानि गरी त्यसले कार्य पुरा गर्न सक्तछ । मानिसले गर्न नसक्ने जोखिमपुण कार्यहरु गर्ने वाक्क लाग्ने झन्झटिला कार्यहरु पुरा गर्ने र तर्कपुर्ण कार्यहरु गर्ने क्षमता भएको यन्त्र कम्प्यूटर हो ।कम्प्यूटरले आकाश, समुद्र तथा धरातलमा बसी चौबीसौ घण्टा कार्यमा एकचित्त भई मानिसलाई साथ दिने साधनको रुपमा सहयोग गर्न सत्तछ । आज जसरि टेलिफोन, टेलिभिजन, हवाइजहाज, मोटर, मोटरसाइक्ल, प्रिन्टिङ प्रेस तथा टाइपराइटरले जुनसुकै पेसामा लागेका व्याक्तीहरुलाई साधनको रुपमा कार्यगरि सहयोग पु¥याइदिन्छ त्यसैगरी कम्प्यूटरले पनि मानवजातिलाई कुनचाहि काममा सहयोगगर्न सत्तैन भन्न गाह्रो भएको छ । त्यसैले आजकाल युरोपतिरू”computerispen”भन्ने कुरो प्रचलित छ ।अव यसको महिमा गएर साध्य छैन।यसकारणडाक्टर,इन्जिनियर,मेनेजर, डाइरेक्टर,प्रोफेसर, अनुसन्धानकर्ता, शिक्षक, विद्यार्थी,गणितज्ञ,वैज्ञानिक, व्यापारी, उद्योगी, खेलाडि तथा अन्य जोसुकैलाई पनि कम्प्यूटर अत्यन्तै उपयोगि साधन कलमजस्तै हुन थालेको छ । त्यसकारण यसको महत्व जताततै बढ्न थालेको छ । अब हाम्रो मुलुकमा पनि एक उपयोगि साधनको रुपमा यसको प्रयोग हुन लागेको छ ।
कम्प्युटर बाट हुने फाईदास्(ADVANTAGE OF COMPUTER)
कम्प्युटर एक असाध्यै, छिटो, शुद्ध र जटिल गणितीय कार्य गर्न सक्ने इलेक्ट्रोनिक यन्त्र हा ।
हजारौँ किलोमिटर टाढा रहेका रेकर्ड वा तालिकालाई आफ्नो पर्दामा ल्याउन, प्रशोधन गर्न र प्रयोग गर्न सक्ने यन्त्र हो ।
अरबौँ करोड अङ्क वा अक्षरहरु मुठ्ठिभरको ठाउँमा अटाउन, क्रम मिलाई राख्न र सम्पादन गर्न सक्ने एक भण्डार हो । अर्को शब्दमा भन्ने हने भने प्रोग्रामबाट निर्देशित लक्ष्य अनुसार तर्कपुर्ण कार्यहरु गर्न सक्ने क्षमता भएको एक यन्त्र हो ।
बराबर दोहोरिरहने, झंझट लाग्दा कार्यहरु वर्षौसम्म, नथाकी गरिरहन सक्ने यन्त्र हो ।
मानिसको कार्य क्षमता, स्मरण शक्ति तर्कपुर्ण सोचाइमा वृद्धि गरी सहयोग पु¥याउने विद्युतीय यन्त्र हो ।
इनपुट लिएर प्रोग्रामअनुसार सम्पादन गरी (output) प्रस्तुत गर्ने एक बहुरुपी यन्त्र हो ।
Advantages of computer
1. It can work very fast.
2. It can give accurate results.
3. It can store large amount of data for future use.
4. It can work nonstop for a long time.
5.It can work automatically
6. It can be used in many fields and applications.
Disadvantages/Limitations of computer
1. It is expensive machine.
2. It is not affordable by everyone.
3.It cannot work itself. It needs user for operating.
4.It needs skilled manpower to operate.
5.It cannot think rationally like human being can do.
6.It only does the work that is instructed.
कम्प्यूटरका बिशेषताहरु Characteristics of computer
१. स्वचालन (Automatic)
२. कार्य बेग (Speed)
३. सुद्धता (Accuracy)
४. डाटा भण्डार (Storage)
५. मेहनती लगनशील (Diligent)
६. विविधकार्य क्षमता (Versatility)
१. स्वचालन (Automatic)
कम्प्यूटरलाई ठीकबेठीक निर्देशनहरु दिन सकिएमा यसले Automatic कार्यहरु गर्न सक्छ डाटा र प्रोग्राम भण्डार गरिएका कम्प्यूटरमा मानिसले चाहेमा यसलाई लगातार कामहरु गर्न लगाई राख्न सकिन्छ ।
२. कार्य बेग (Speed)
कम्प्यूटरले काम अत्यन्तै छिटो गर्न सक्छ अर्थात एक सेकेन्डमा हजारौ, वा करोडौ निर्देशनहरु पालना गर्न सक्छ । साधारणतया यसको कार्य क्षमतालाई सेकेन्डमा नाप्ने चलन छ ।
कम्प्यूटरका ईकाइ
१. मिलीसेकेन्ड एक हजार भागको एक खण्ड
२. माइक्रो सेकेन्ड दस लाख भागको एक खण्ड
३. नानो सेकेन्ड एक अरब भागको एक खण्ड
४. पिको सेकेन्ड दस खरव भागको एक खण्ड
५. फेप्तो सेकेन्ड दस निल भागको एक खण्ड
Unit of time Meaning Part of second power
Millisecond(ms) One thousandth of a second 1/1000 sec 〖10〗^(-3)
Microsecond(us) One millionth of a second 1/1000000 sec 〖10〗^(-6)
Nanosecond (ns) One billionth of a second 1/1000000000 sec 〖10〗^(-9)
Pico second(ps) One trillionth of a second 1/100000000000 sec 〖 10〗^(-12)
३. सुद्धता (Accuracy )
कम्प्यूटरले हिसाब गरी निकाल्ने नतिजा सत प्रतिशत ठीक हुन्छ । हामीले गलत प्रोग्राम वा गलत सुत्र वा गलत डाटा दिएमा मात्र गलत उत्तर निकाल्दछ । अन्यथा यसले गर्ने हिसाब गलत हुदैन ।
४. डाटाभण्डार(Data Stroage)
कम्प्यूटरभित्र डाटा भण्डार हुने ठाउँलाई Hard Disk भन्दछ । हुन त बाहिरपट्टि कम्प्यूटरले आफ्नो डाटाहरु टेप,फलपी डिस्क र सीडीरोम डिस्कमा पनि भण्डार गर्दर्छ । यी सबैलाई डाटा भण्डार गर्ने ठाउँको रुपमा लिइन्छ । यिनिहरुमा कतिओटा डाटा वा रेकर्डहरु
अड्छन भनी क्षमताको नाप गर्न एउटा Unit आबस्यतmा पर्दछ डाटा भण्डार गर्ने क्षमता Byte मा नापिन्छ । अर्थात एक बाइट भन्नुको अर्थ एउटा अक्षर वा अङ्क वा चिन्ह हो ।
जस्तै ( A,B,C,D,1,2,3,4 + – ईत्यादि०
५. मेहनती (Diligent)
कम्प्यूटरले काम गर्दा बढी एकाग्रता कायम गर्न सक्छ । यसलाई जुन काम दियो उता हेरी एकैनासले त्यो काम धेरैपटक दोहो¥याई,तेहा¥याई गरी रहने गर्दछ । उक्त कार्य गर्दा यसले शुद्ध नतिजा ल्याउन उच्च वेगमा बिना रोकावट कार्य गरिरहन्छ । मानिसले काम गर्दा थकित हुने ,गल्ती नतिजा निकाल्ने तथा अल्छी गर्ने हुन्छ तर कम्प्यूटर कहिल्यै ढिला गर्ने,गल्ती तथा अल्छी गर्ने काम गर्दैन । यसको महत्व यसैमा छ ।
६. विविध कार्य क्षमता (Versatility)
कम्प्यूटर एउटा यस्तो मेशिन हो जसले धेरै थरिका कामहरु गर्न सक्छ । कम्प्यूटरले हिसाब गर्ने, लेखा छाप्ने, ग्राफ खिच्ने, लेखा राख्ने, नक्सा कोर्ने, फोटो खिच्ने, चिठिपत्र आदानप्रदान गर्ने, रोग निरिक्षण गर्ने, बैज्ञानिक कार्य गर्ने, बैकिङ्ग कार्य गर्ने, शिक्षक बनी पढाउने रिजल्ट तयार गरिदिने लगायतका धेरै कामहरु गर्न सक्छ त्यर्सैले कम्प्यूटर एउटा विविध कार्य क्षमता भएको मेशिन हो ।
कम्प्युटरको बर्गीकरण
हामीले फरक–फरक प्रकारका कम्प्युटर प्रयोग गर्दछौ कम्प्युटर हरुमा फरक– फरक कामका
लागी फरक–फरक खालका कम्प्युटर उत्पादन गरेका छन् । त्यसैले आज हामिले बजारमा धेरै
थरीका कम्प्युटर देख्न सक्छौ ।
कार्य अनुसार ( On The basic software)
कार्य अनुसार कम्प्युटर मुख्य तिन प्रकारका छन् ।
१.एनालग कम्प्यूटर -Analogue computer_
यो यास्तो कम्प्यूटर हो जसले गणना को सट्टा कुनै पनि इकाइ नापेर वा मानिरले जस्तै कार्य गर्न सक्दछ ।
यस्तो कम्प्यूटरलाई एनालग कम्प्यूटर भनिन्छ । ग्रिक शब्द “एनालग” बाट एनालग कम्प्यूटर भन्ने नाम राखिएको हो । ट्याक्सी मा चढ्दा जति जति टाढा गयो उति उति मिटरमा पैसा थपिदैं जान्छ । त्येस्तै मोटर साइकलमा त्यसको गुडने वेग बढदै जाँदा २०,३०,वा ४० गति किलोमिटर वेगका साथ बढदै जान्छ । त्यसलाइ स्पोडोमिटर को सुईले देखाउदै जान्छ । पेट्रोल पम्प बाट पेट्रोल वा डिजल खन्याउदै जाँदा लिटरको संख्या बढदै जान्छ । यस्ता कम्प्यूटरलाई एनालग मेसिन भनिन्छ । अन्तर्देशिय टेलिफोन प्रयोग गर्दा लागेको समय नाप्ने यन्त्र लाइ पनि एनालग कम्प्युटर भन्दछन् ।
२.डिजिटल कम्प्यूटर (Digital Computer)
वाईनरि डिजिटल (O र I)मा आधारित कम्प्यूटरहरुलाई डिजिटल कम्प्यूटर भनिन्छ ।
यस्ता कम्प्यूटरहरुले कुनै पनि नाप नाप्नको सट्टा संख्या गरेर कार्यगर्ने गर्दछ । आज संसार
भर प्रयोग भएका ९०% कम्प्यूटर डिजिटल छन् ।
३. हाइब्रिड कम्प्यूटर (Hybrid computer)
एनालग र डिजिटल कम्प्यूटरले गर्ने काम एउटै कम्प्यूटरले गर्न सक्ने गरि बनाईएको कम्प्यूटरलाई हाइब्रिड कम्प्यूटर भनिन्छ । हाइब्रिड कम्प्यूटर खास गरि अस्पताल, कारखाना, बैज्ञानीक कार्यशाला, हवाईजहाज, रकेड आदिमा जडान गरिएका हुन्छन ।
आयतन अनुसार९इल (On The Basisatuolume )
आयतन अनुसार कम्प्युटर मुख्य चार भागमा बर्गिकरण गरिएको छ ।
१. सुपर कम्प्यूटर (Super Computer)
सुपर कम्प्यूटर सवै भन्दा शत्तीशालि कम्प्युटर हो । यसको साईज ठुलो हुन्छ । प्रोसेशिङ्ग गति पनि निकै बडि हुन्छ । यस्ता कम्प्यूटर खासगरि वैज्ञानिक अनुसन्धानहरु जस्तै न्यूक्लियर फिजन ,न्यूक्लियर चेक रियाक्सन आदि कामको लागी प्रयोग गरिन्छ
२. मेनफ्रेम कम्प्यूटर (Mainframe Computer)
मेनफ्रेम कम्प्यूटर आयतनको हिसाबले निकै ठुलो हुन्छ । करिव १ हजार वर्ग फिट ठाँउ लिन्छ । यो निकै शक्तीशाली र प्रोसेसिङ्ग गति निकै बढी भएको कम्प्यूटर हो । यस कम्प्यूटरबाट एकै पटक ४००÷५०० ओटा कम्प्यूटर टर्मिनलमा डाटा इन्ट्री गर्न । वा डाटा प्रोसेसिङ्ग गर्न सकिन्छ । यस्ता कम्प्यूटरमा एकै समयमा सयौँ मानिसहरुले काम गर्न सक्छन् । यसको मुल्य पनि निकै धैरै छ । यसले सम्पूर्ण नेटवर्किङ्गमा भाग लिन सक्छन्।
३. मिनि कम्प्यूटर (Mini Computer)
मिनि कम्प्यूटर मेनफ्रेम कम्प्यूटर भन्दा कम शक्तीशाली र माईक्रो कम्प्यूटर भन्दा बढि शक्तीशाली हुन्छन् । यस कम्प्यूटरमा पनि सयौ टर्मिनलहरु जोडेर यसबाट काम गराउन सकिन्छ । यी कम्प्यूटर हरु मुख्य गरि डाटा प्रोसेसिङ्ग ,प्रोग्रामिङ्ग र डेक्सटप जस्ता कार्यहरुमा प्रयोग गरिन्छ ।
४.माईक्रो कम्प्यूटर (Micros Computer)
माईक्रो कम्प्यूटर आयतनको हिसावले सबभन्दा सानो कम्प्यूटर हो । यो कम्प्यूटर माईक्रो चिप्स (Microchips)प्रयोग गरेर बनाइएको हुनाले यसको नाम माइक्रो कम्प्यूटर रहेको हो । माइक्रो कम्प्यूटर लाई प्रसनल वा home कम्प्यूटर भनिन्छ । यो कम्प्यूटर घर ,अफिसमा मूख्य गरि आवश्यक छ । आज भोली धेरै जसो क्षेत्रहरु जस्तै व्यापार, व्यवसाय, शिक्षा सञ्चार हरुमा प्रयोग गरिन्छ ।
Computer ले कसरि काम गर्दछ ?
How does a computer work?
कम्प्यूटरले काम गर्नको लागि हार्डवेयर Hardware र सफ्टवेयर Software को मिलन हुनुपर्छ । Hardware भन्नाले कम्प्यूटरका बिभिन्न भागहरु जस्र्तै सि.पि.यू,मनिटर,प्रिन्टर,किबोर्ड,माउस,इत्यादि लाई बुझिन्छ । जसलाई हामीले आखाले देख्न र हातले छुन सक्छौ । Software भन्नाले कम्प्यूटर ले बुझ्ने भाषामा क्रमबद्ध गरि लेखीएका निर्देशनहरुका विभिन्न सेटहरु लाई सफ्ट्वेयर भनिन्छ । जसलाई हामीले हातले छुन सक्दैन ।
कम्प्यूटर ईनपुट प्रोसेस र आउटपुट (IPO) सिद्धान्त अनुसार काम गर्दछ ।
इनपुट प्रोसेसर आउटपुट
३०+९० प्रोसोधन प्रोसेसर सिपियु १२० परिमाण
डाटा आउटपुटसाधन हरु
ईनपुटसाधानहरु मनिटर
किवोर्ड प्रिन्टर
माउस
स्क्यानर स्पिकर
माईक्रोफोन
डिजिटल÷ वेब क्यमरा .
कम्प्यूटर संचालन गर्ने तरिका
कम्प्यूटर एउटा मेसिन हो जसले प्रयोगकर्ताले दिईएको निर्देशनअनुशार काम गर्दछ । कम्प्यूटरलाई काम गर्नको लागि रेडी गराउनको लागि यसमा जोडिएका सम्पुर्ण भागहरु (Peripherals) राम्रोसंग जोडिएको हुनुपर्छ । अनि सम्पूर्ण हार्डवेयर र सफ्टवेयरहरु बीचमा सम्बन्ध कायम गराउनुपर्दछ । यसरी हार्डवेयर र सफ्टवेयरहरु बीचको एक आपसमा सम्बन्ध कायम गराउन एउटा विशेष प्रकारको सफ्टवेयर आवश्यकता पर्दछ । जसलाई अप्रेटिङ सिस्टम ९(Operating System) सफ्टवेयर भनिन्छ ।
कम्प्यूटर खोल्दा पहिला यसमा U.P.S (on) गर्नुपर्छ । त्यसपछि यसको सुरुवातको लागि प्रोसेस अपरेटिङ सिस्टमबाट सुरु हुन्छ । त्यसपछि हामी कम्प्यूटरका प्रोग्रामभित्र जानका लागि फरक–फरक प्रोसेस छन् । उक्त कुरा तपाईको कम्प्युटरमा राखेको अपरेटिङ सिस्टममा भर पर्दछ । त्यसैले कम्प्यूटर संचालन गर्नुभन्दा अगाडि आफ्नो कम्प्युटरमा राखेको अपरेटिङ सिस्टमको बारेमा ज्ञान हुनु आवश्यक छ ।
विन्डोज अपरेटिङ सिस्टम अन्तर्गत कम्प्यूटर खोल्ने तरिका
स्टेप १ U.P.S (Uninterrupted Power Supply) (ON) गर्नुहोस् ।
स्टेप २ कम्प्युटरC.P.U (Central Processing Unit) को स्विच (ON) गर्नुहोस् ।
स्टेप ३ स्मनिटरको स्विच अन (ON) गर्नुहोस् ।
COMPUTER को अगाडि को भाग ।

सीडी रोम
फ्लोप्पि डिस्क
पावर आँन बटन
रेसेट बटन
यू.एस.बि पोर्ट
साउण्ड पोर्ट
CUMPUTER को पछाडिको भाग
(SMPS) Switch Mode Power Supply
Out Put Power Port (200-240v)
In Put Power Port (200-240v)
Ps/2 Key Board Port (Purpale Colour)
Ps/2 Mouse Port (Green Colour)
Com (Sirial) Port (9pin)
Parllel (Lpt) Port
Display Port (Monitor Cable)
Usb Port (Univarsal Sirial Bus)
LanPort, Net Work Port (Local Aria Network) Rj45 Jack (Connector)
Microphone Input Port (Pink Colour)
Sound Out Put Port (Green Colour)
Microphone Out Put Port (Sky Blue)
CPU Colling Fan
त्यसपछि केही समय पर्खनुपर्ने हुन्छ, जुन समयमा कम्प्युटरले बुटिङ (booting) प्रोसेस गर्दछ ।
बुटिङ (booting) भनेको कम्प्युटर खुल्ने क्रममा हार्डडिस्क वा अन्य स्टोरेज डिभाइसहरु (CD–ROM, Floppy E.T.C.) रहेका सिस्टम फाइलहरु कम्प्युटरको मेमोरी (Memory) मा ल्याउने काम हुन्छ यही प्रक्रियालाई नै बुटिङ भनिन्छ

यस क्रममा मनिटरमा कुनै निर्देशनहरु देखिए भने त्यसलाई पालना गर्दै जनुपर्छ । यदि तपाईको कम्प्यूटर पासवर्ड (Password) सिस्टमबाट लक गर्नुभएको छ भने युजर नेम र त्यसको पासवर्ड टाइप गर्नुपर्दछ ।

विन्डोज ः
परिचय
अपरेटिङ सिस्टम एउटा यस्तो प्रोग्राम हो जसले कम्प्युटर सिस्टमको सम्पूर्ण कृयाकलापलाई नियन्त्रण तथा संचालन गर्दछ । अपरेटिङ सिस्टमहरु धेरै प्रकारका छन् । जस्तैMS Dos, Ms Windows (95/98/2000 Xp Vista Etc) Unix Linux आदि । यि मध्ये आज विश्वका धेरै धेरै भन्दा (प्राय सबै जसो) कम्प्यूटर प्रयोगकर्ताहरुले Windows अपरेटिङ सिस्टम प्रयोग गरेको पाइन्छ यो माइक्रोसफ्ट कम्पनीले उत्पादन गरेको अपरेटिङ सिस्टम हो ।
यस कम्पनिले विन्डोज् अन्तरगतका धेरै भर्सनहरु उत्पादन गरि सकेको छ । जसमध्ये गरि सकेको छ । जसमध्ये Windows Vista यस कम्पनीले हालै मात्र उत्पादन गरेको निकै एड्भान्स फिचहरु र सुविधाहरु उपलब्ध भएको अपरेटिङ सिस्टम हो । यसको प्रयोग भर्खरै मात्र सुरु भएको छ । विन्डोज एक्स पि.मा यस भन्दा अगाडि रिलिज गरिएका विन्डोज भर्सनहरुमा भन्दा निकै धेरै एड्भान्स फिचरहरु उपलब्ध छन् । जसले गर्दा हामीलाई कम्प्यूटर संचालन गर्न निकै सजिलो भएको छ ।यसले DOS तथा Windows मा आधारित सम्पूर्ण प्रोग्रामहरुलाई छिटो तथा सजिलैसंग रन गराउन सक्दछ । यसमा निकै एड्भान्स र शक्तिशालि मल्टिमिडिया तथा नेटवर्किङका फिचरहरु छन् ।यसले इन्टरनेट ई–मेल अडियो भिडियो च्याट भ्वाइस च्याटका लागि निकै सजिलो गराएको छ । त्यसैले आजकाल कम्प्यूटर प्रयोगकर्ताहरु Windows XP नै प्रयोग गर्ने गर्दछन् ।
त्यसपछि तपाई सिधै विन्डोज भित्र जान सक्नुहुनेछ । जसको सहायताले तपाईले कुनै पनि काम गर्न सक्नुहुन्छ । कम्प्यूटर खुल्नासाथ देखिने विन्डोजको चित्र यहाँ देखिएको छ ।